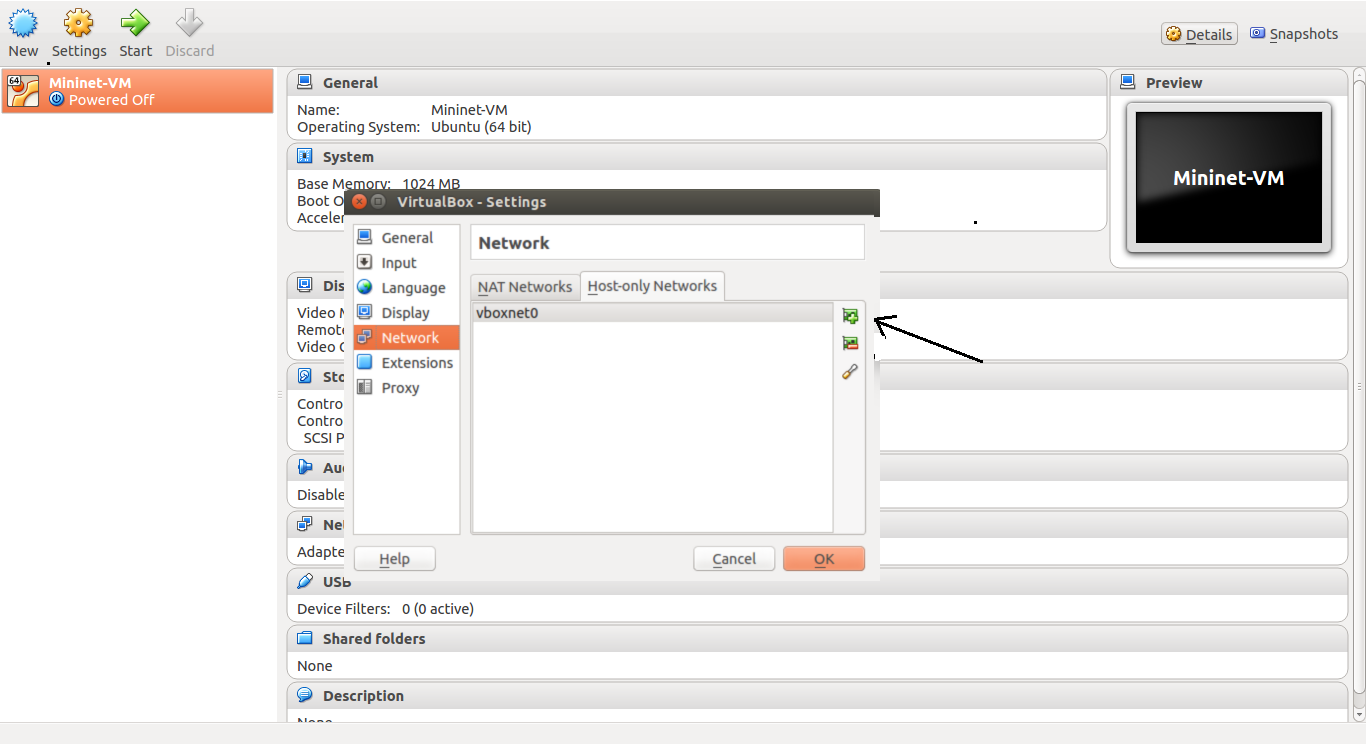
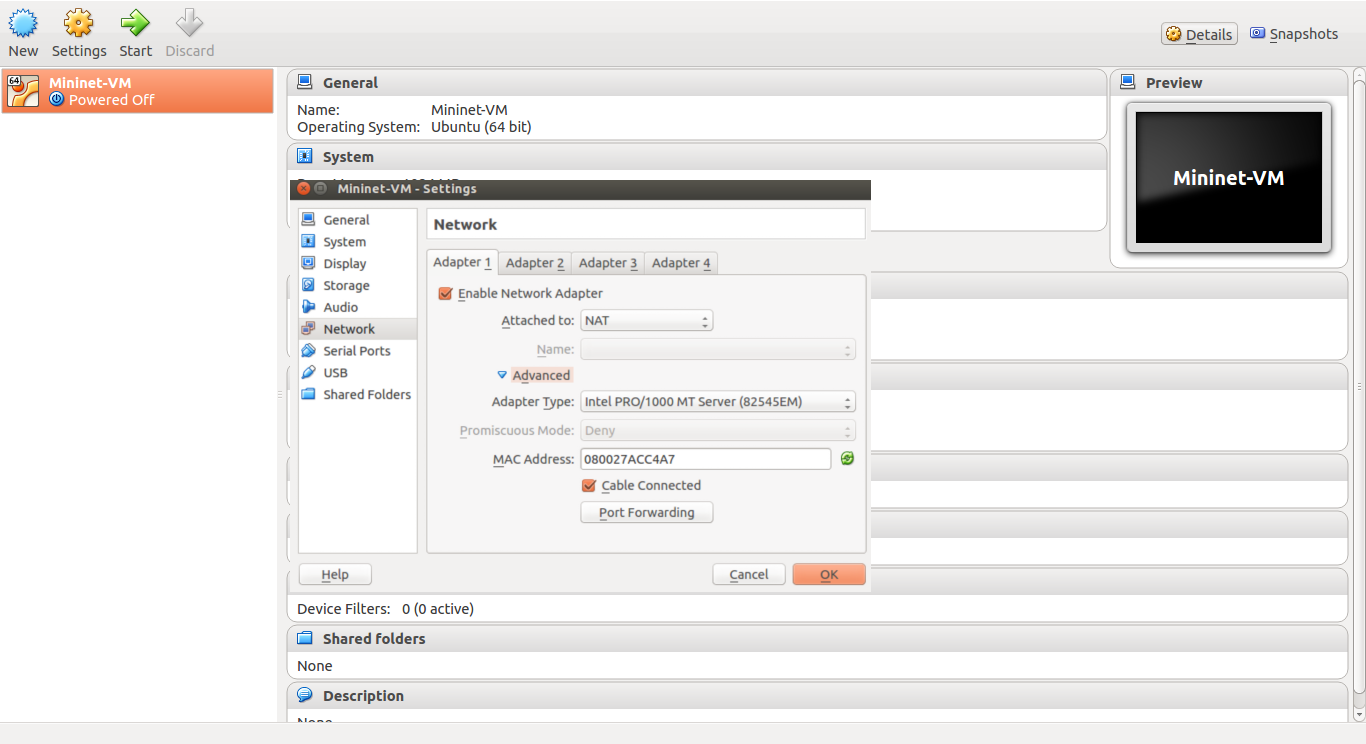
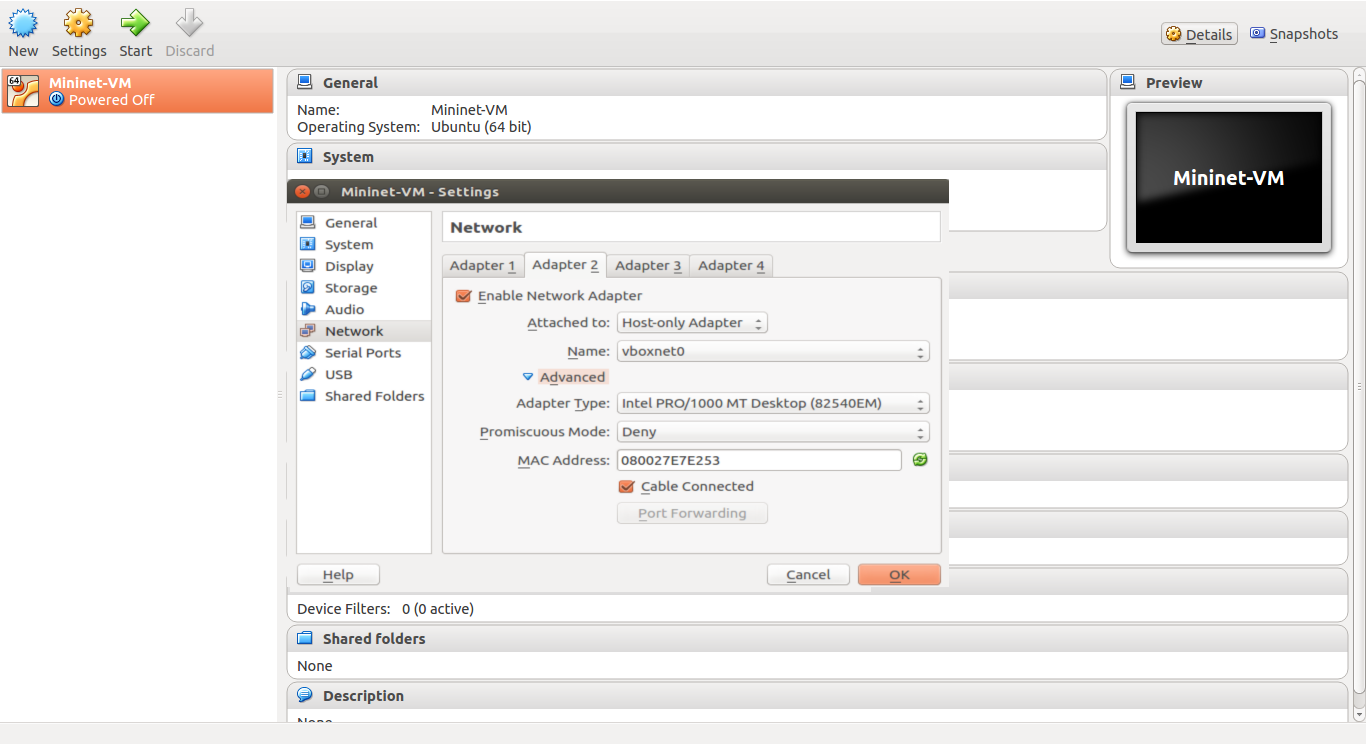
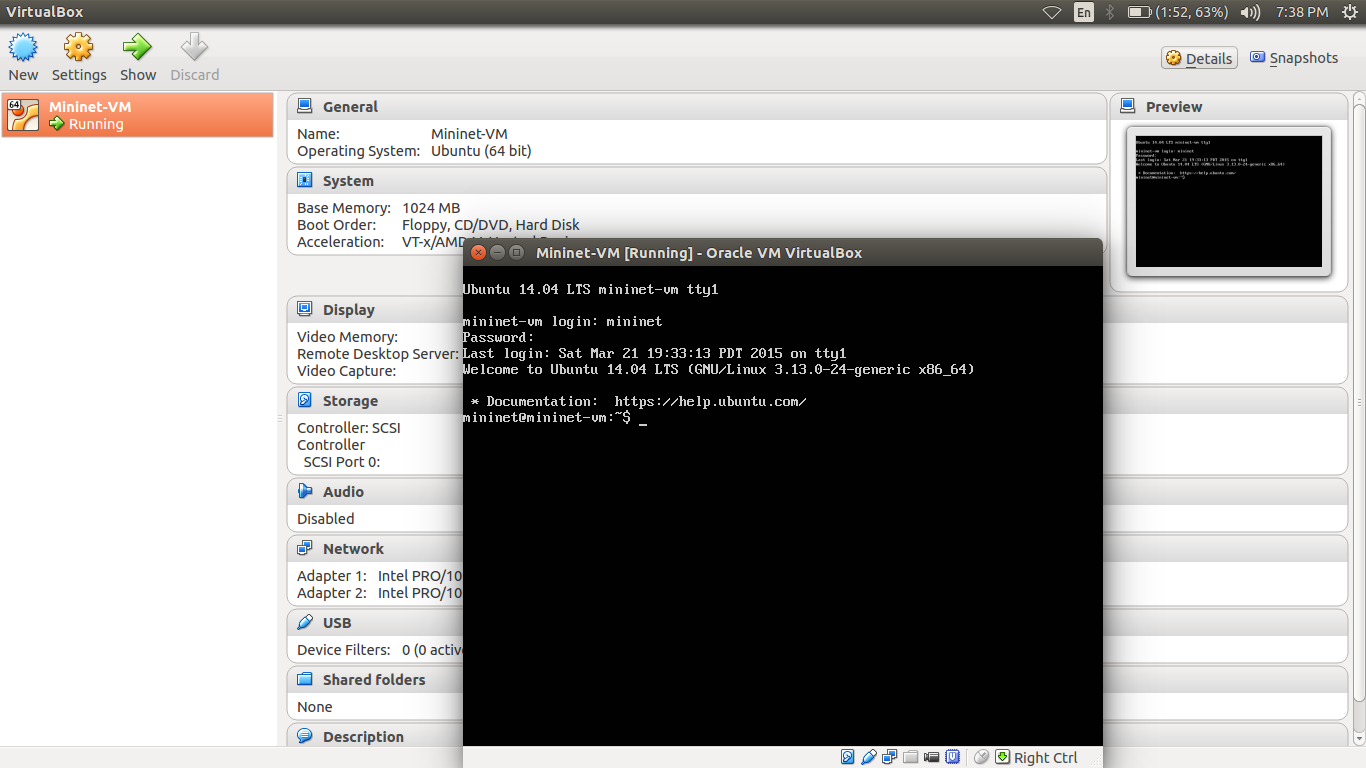
Note: Google Drive links may not work or might be expired. You can find the scripts here
Tutorial no 11
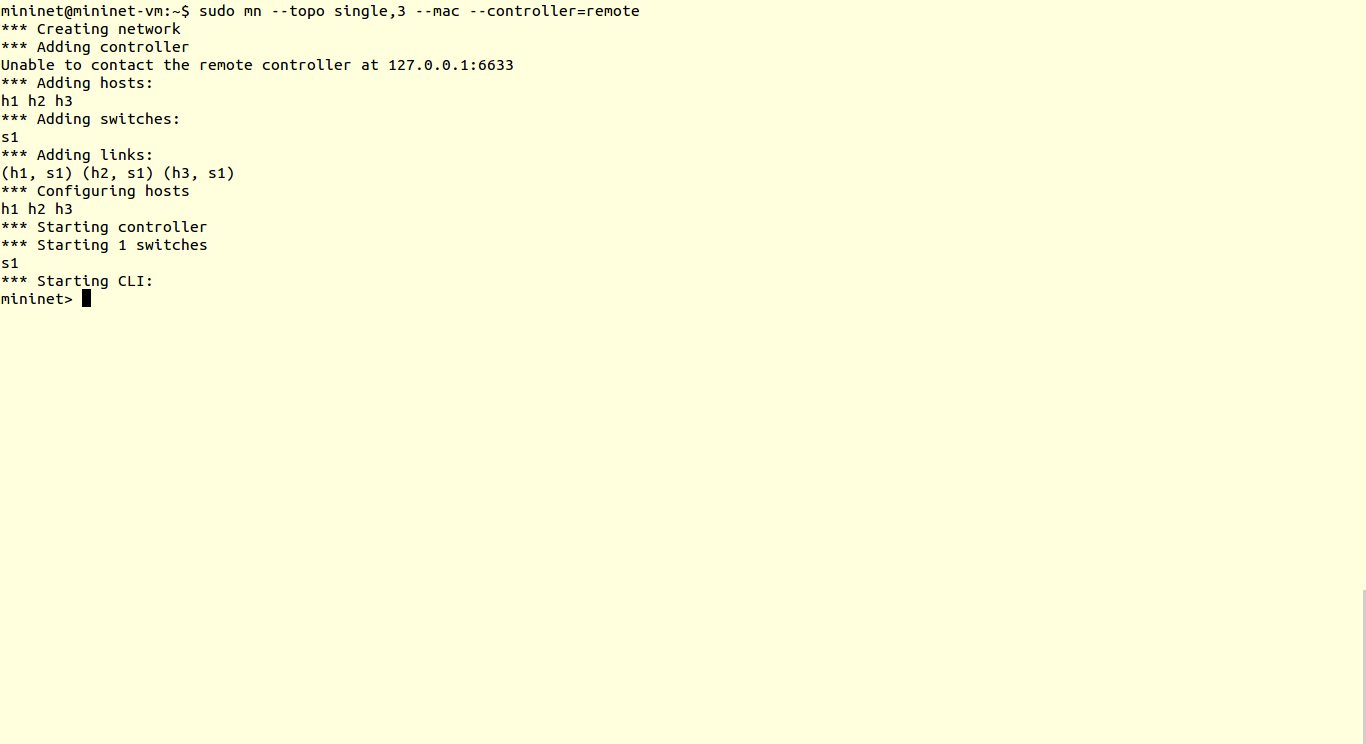
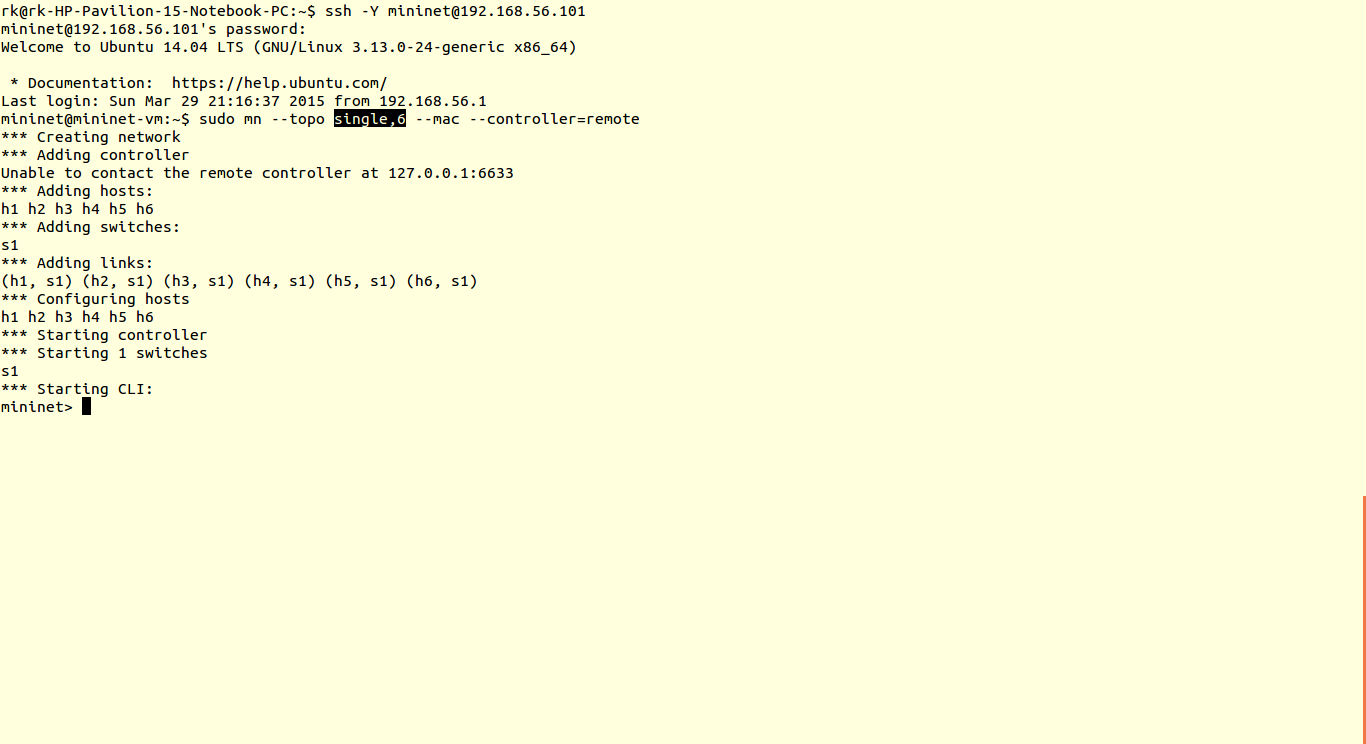
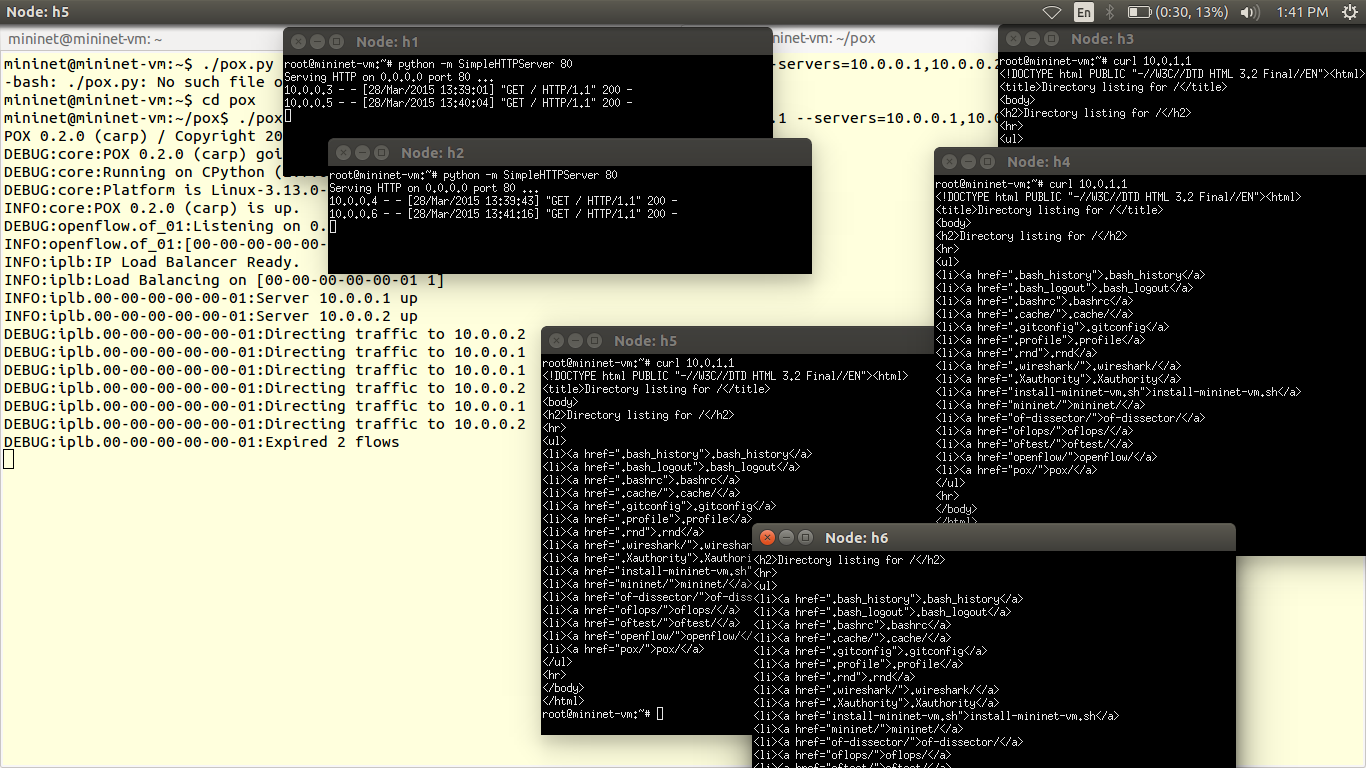
So, in all the tutorials we covered before, we have used default controller scripts & default topologies. In this tutorial we are going to design our custom topology and custom controller scripts.
You will find this tutorial very interesting, because till now we have created topologies in Command Line Interface ofMininet. And here we have Graphical Interface. We will use cloud application called VND (Virtual Network Descriptor) to create topology and controller script. This VND tool is developed by Ramon Fontes, Federal Institute of Bahia, Brasil and available on
www.ramonfontes.com/vnd (Note:- You should have updated flash player in your system to work with VND)
1) Visit above link to getting started with VND.
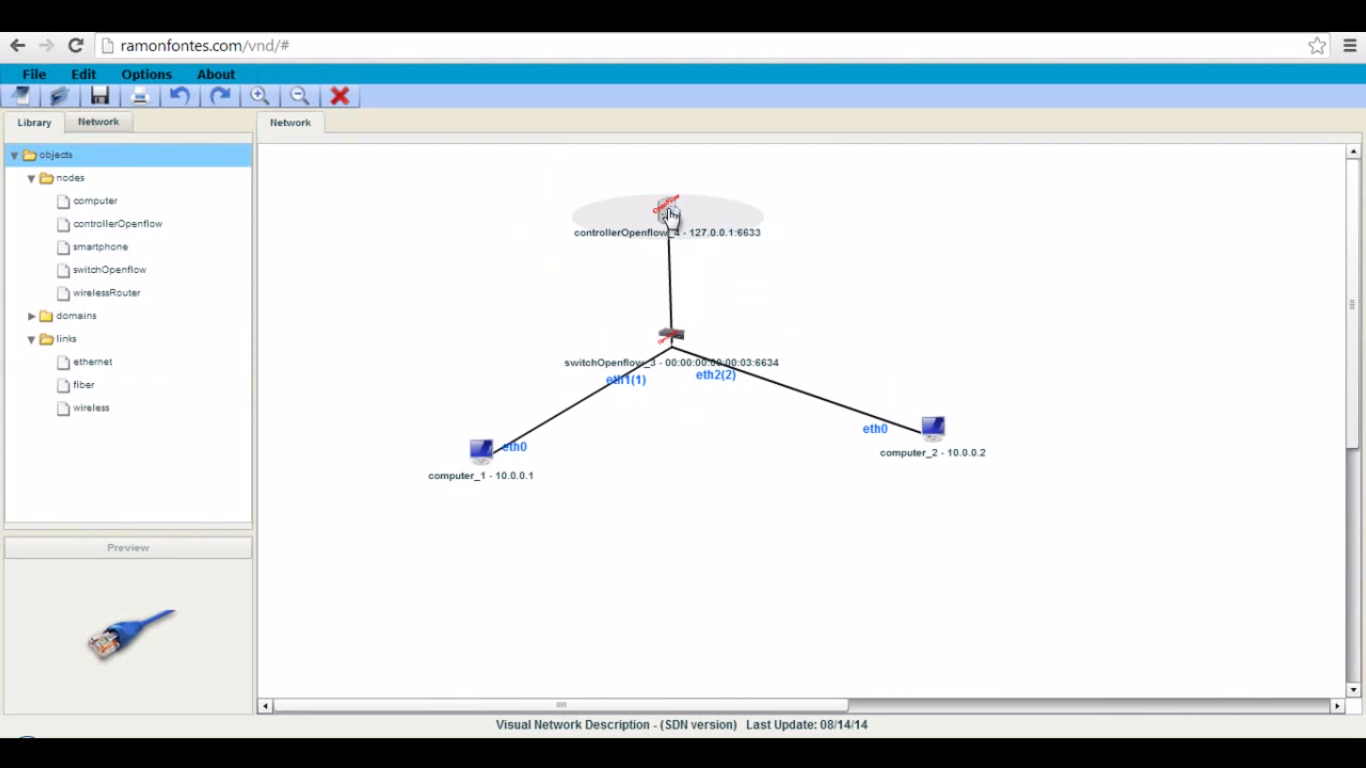
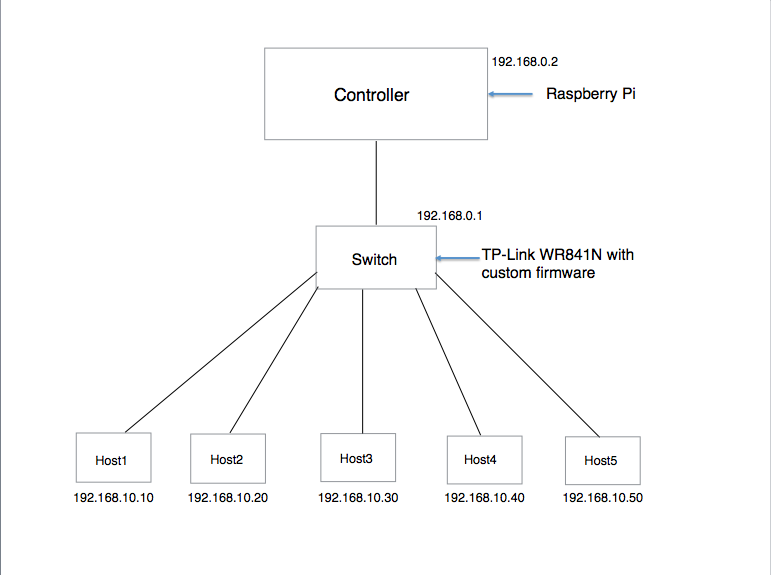
2)To create topology, select hosts, OpenFlow switch and OpenFlow controller. Use Ethernet links to connect hosts.
3) After that lets focus on controller configuration. Now we will define simple flow rule for host1 and host2 traffic.
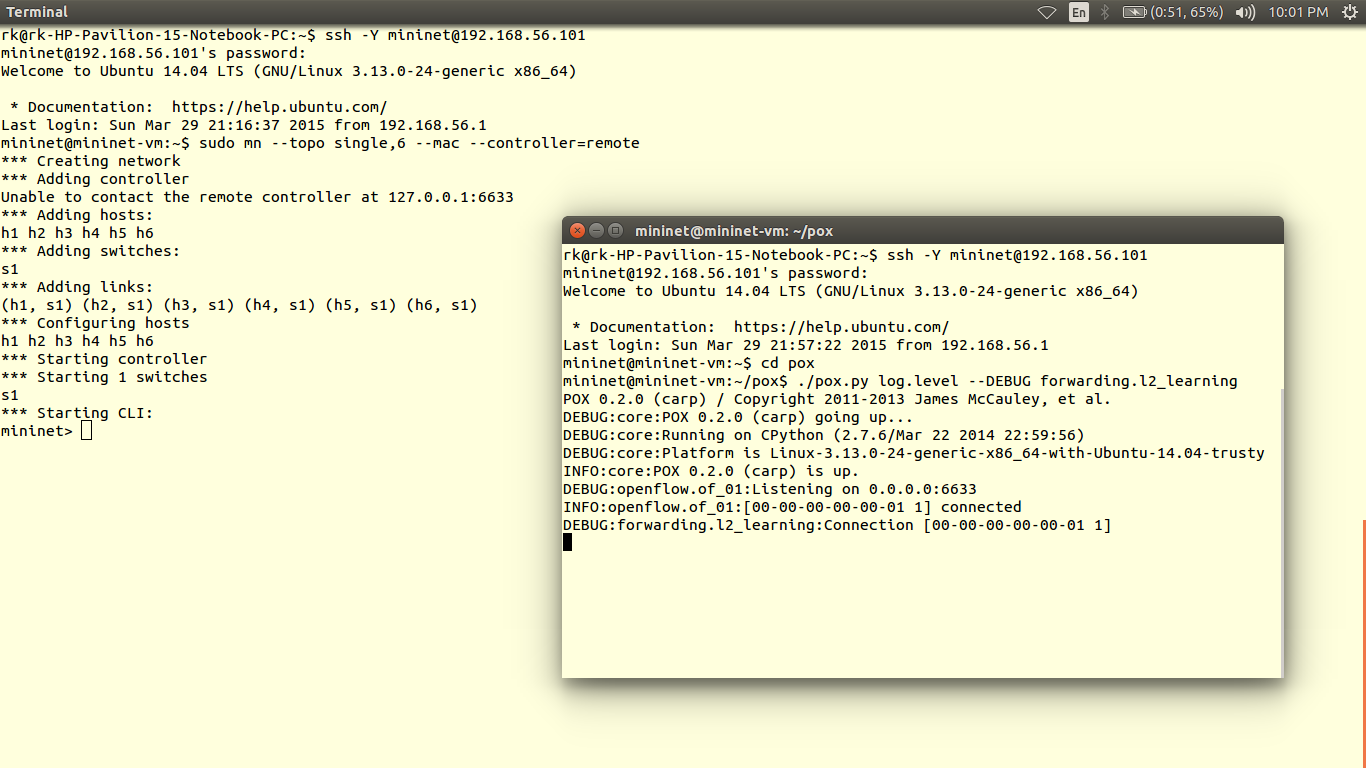
Select controller POX
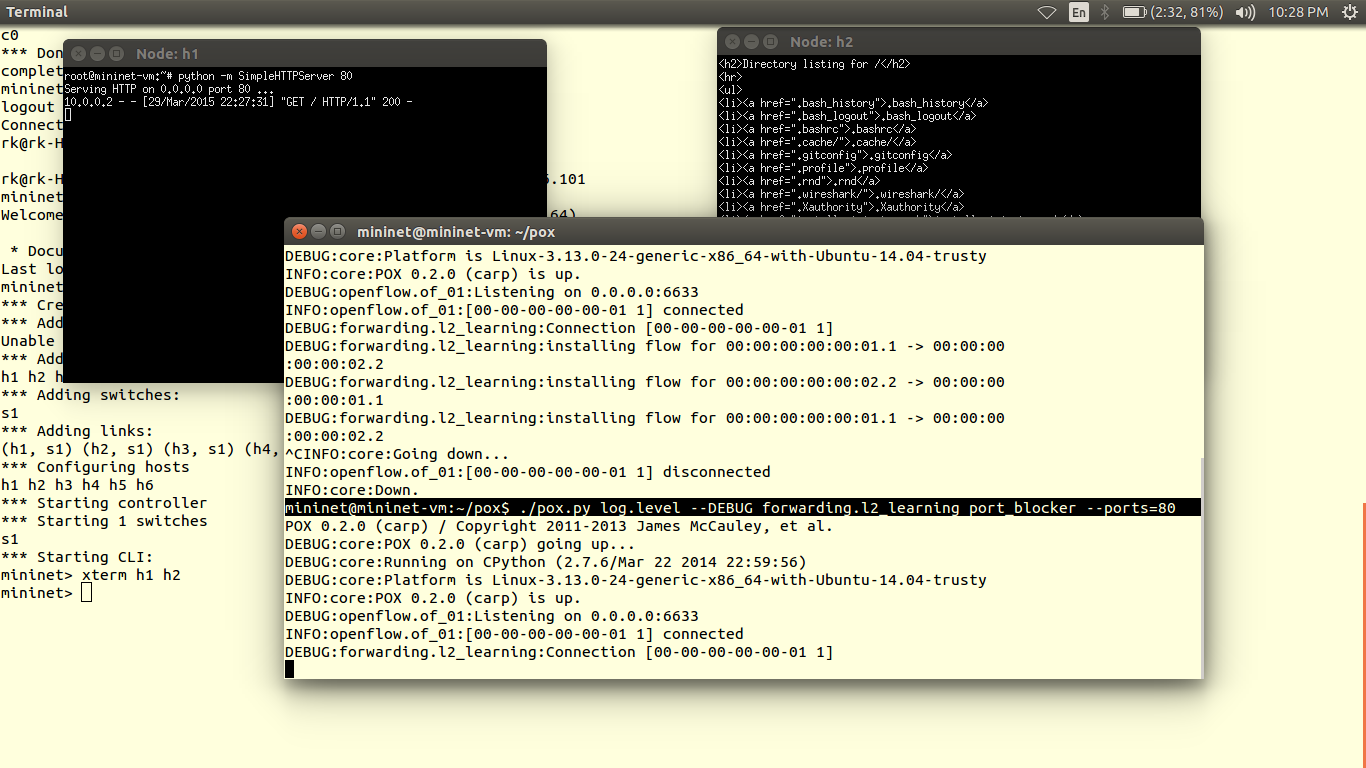
Ingress port=1, Output=2 # packets coming from port 1 are forwarded to port 2 Ingress port=2, Output=1 # packets coming from port 2 are forwarded to port 1
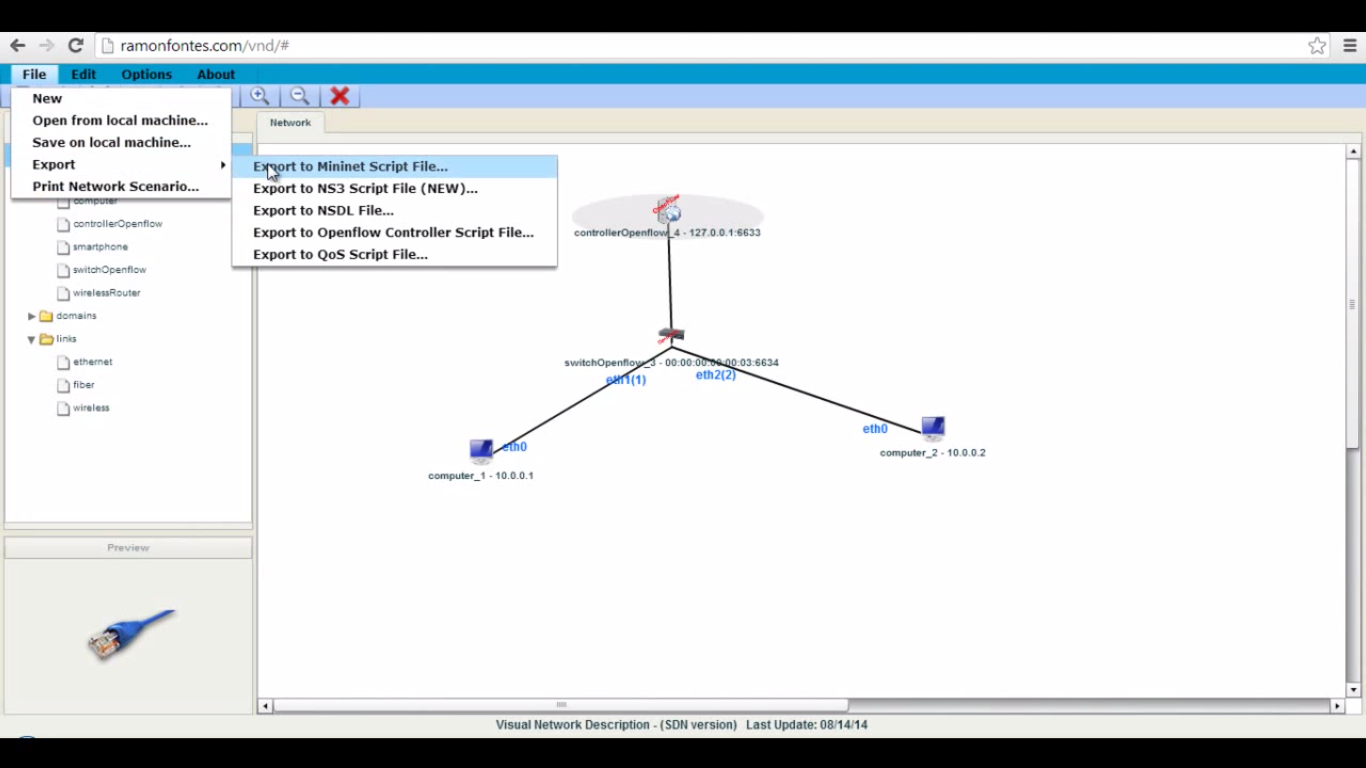
4) After all configurations, download the both topology and controller scripts.
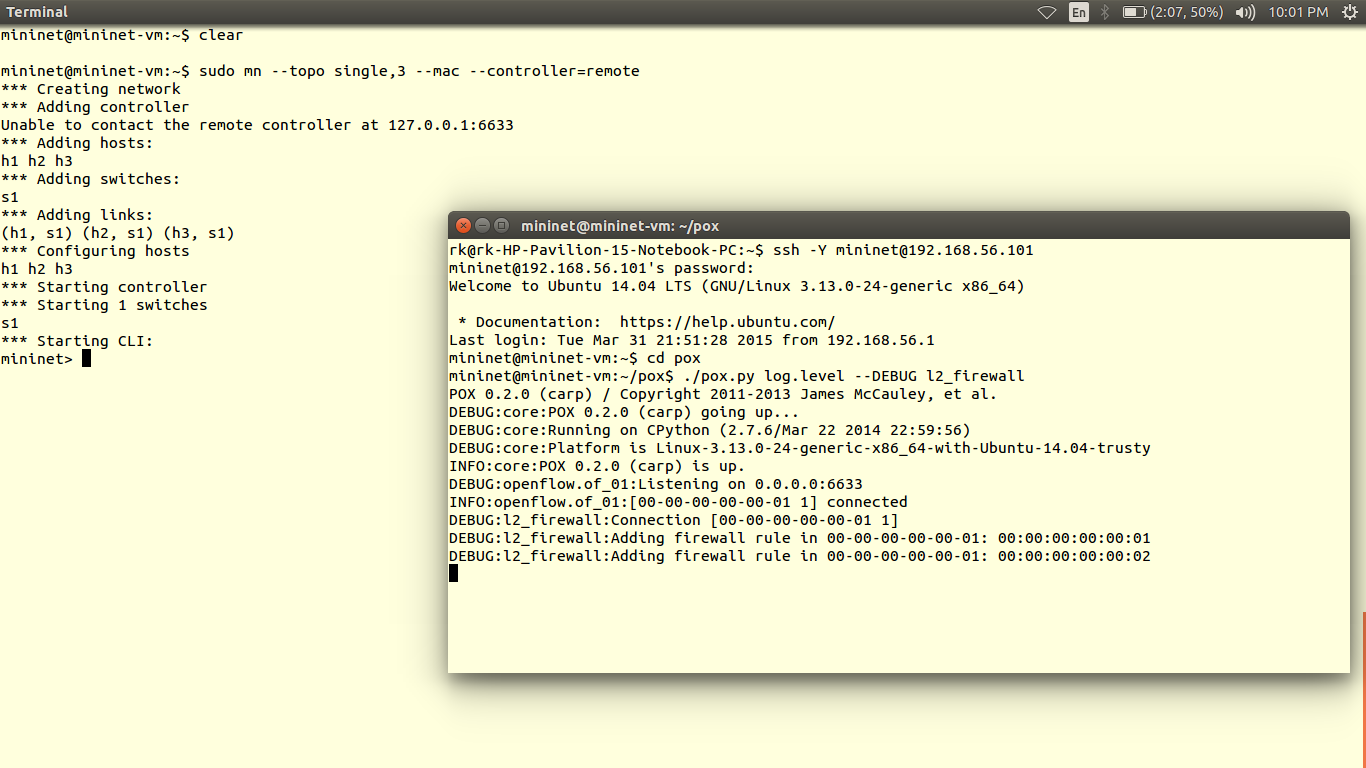
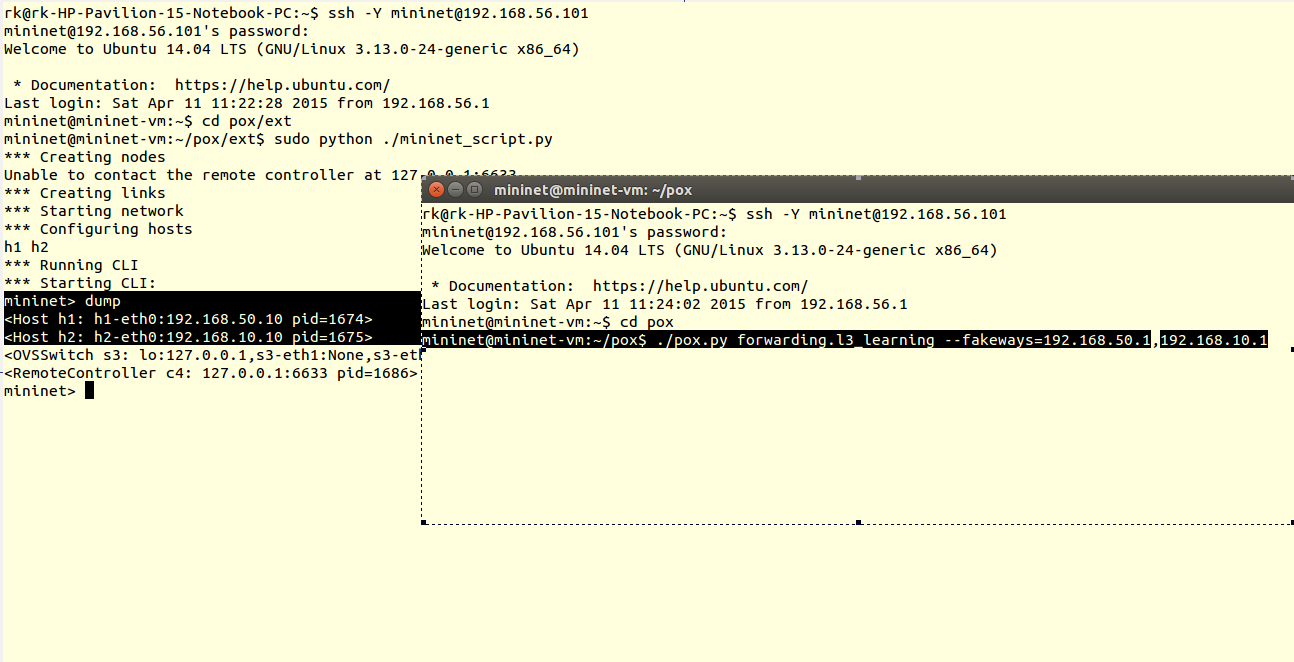
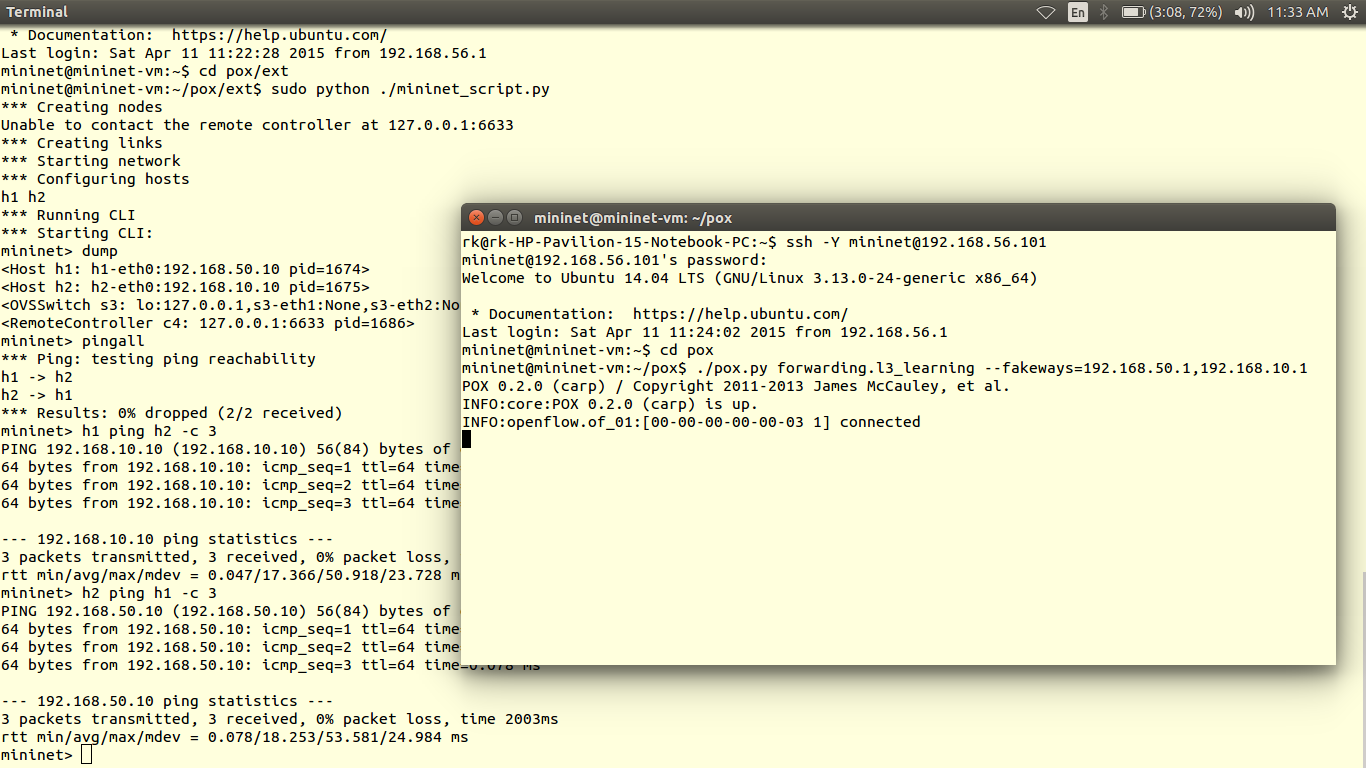
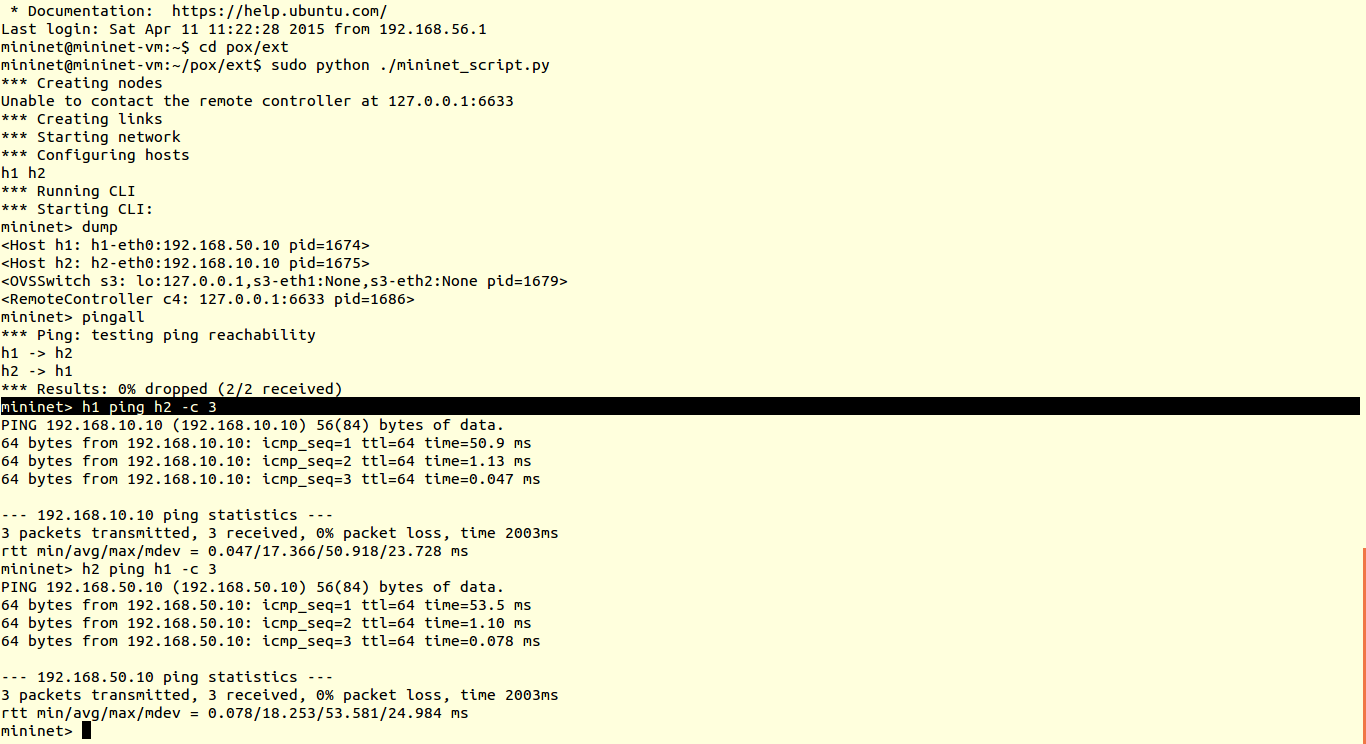
5) Then as usual save the scripts in pox/ext folder and run it
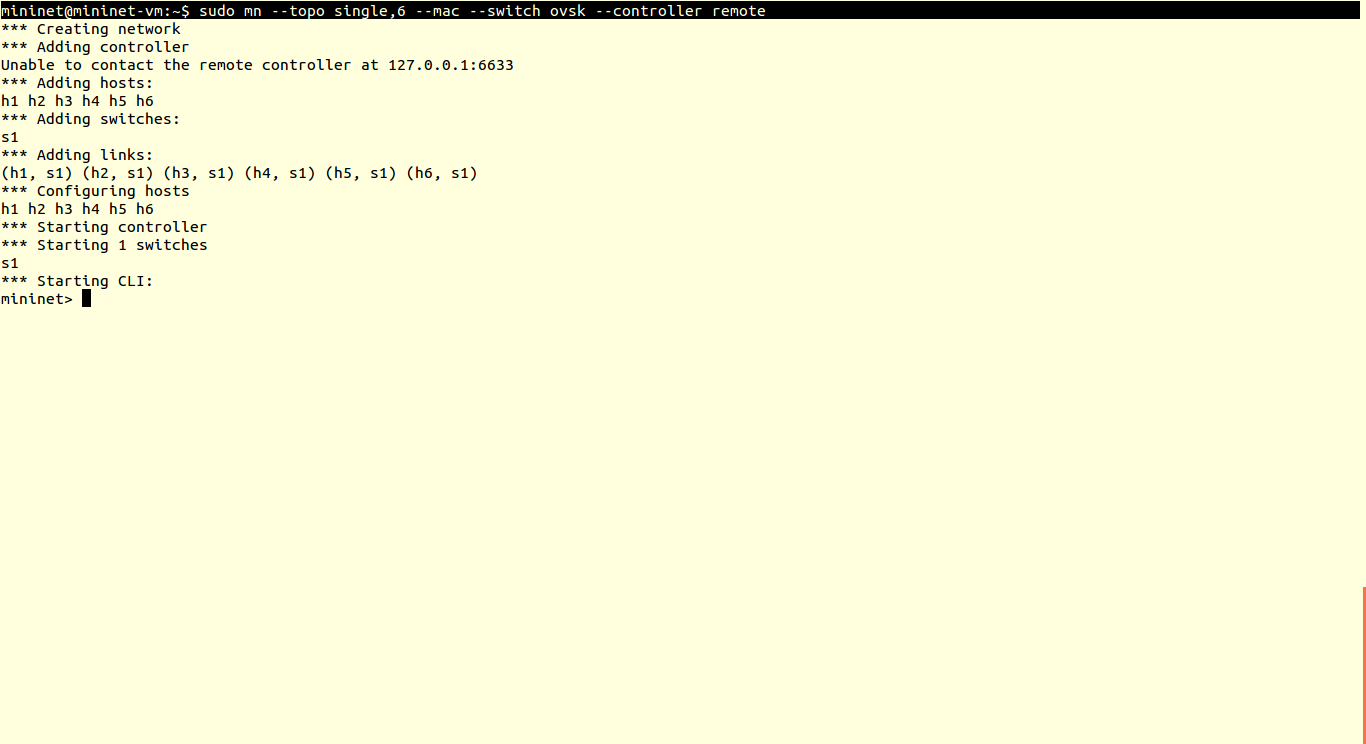
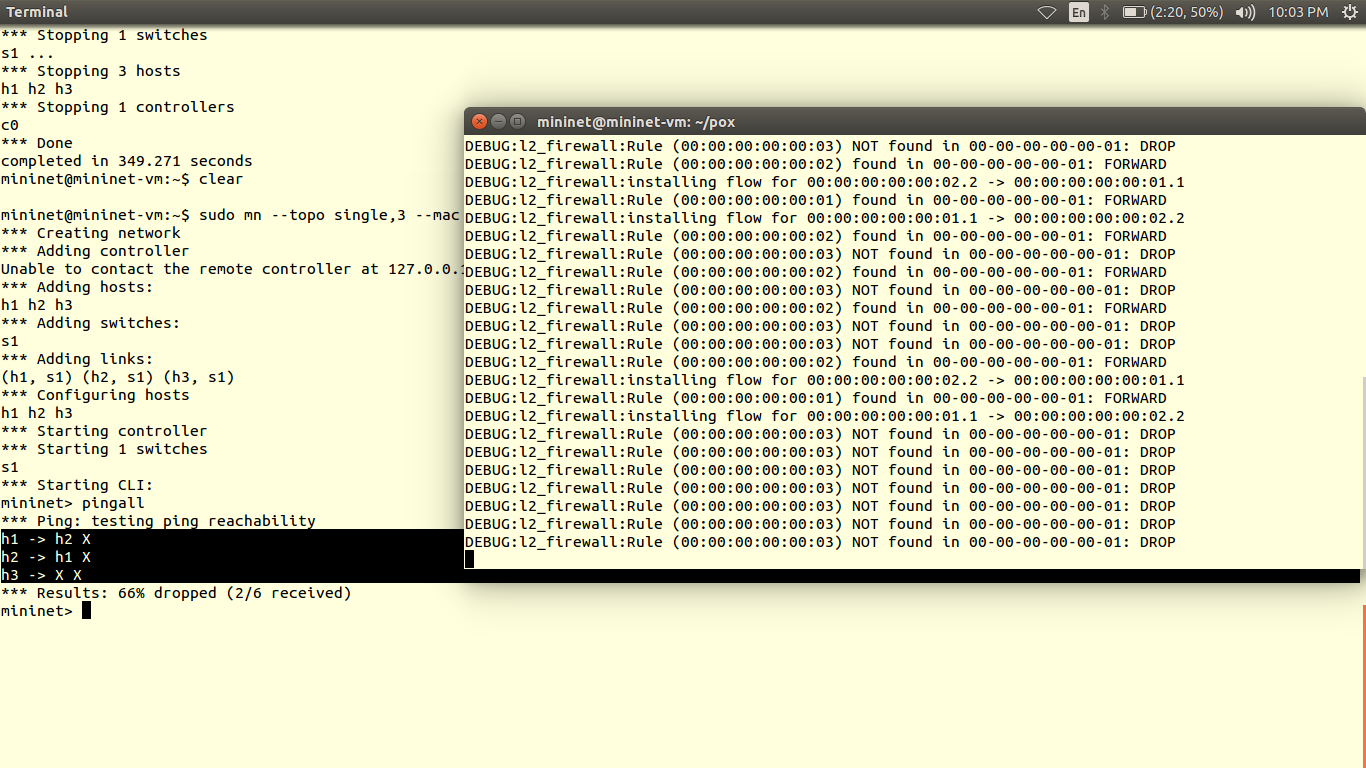
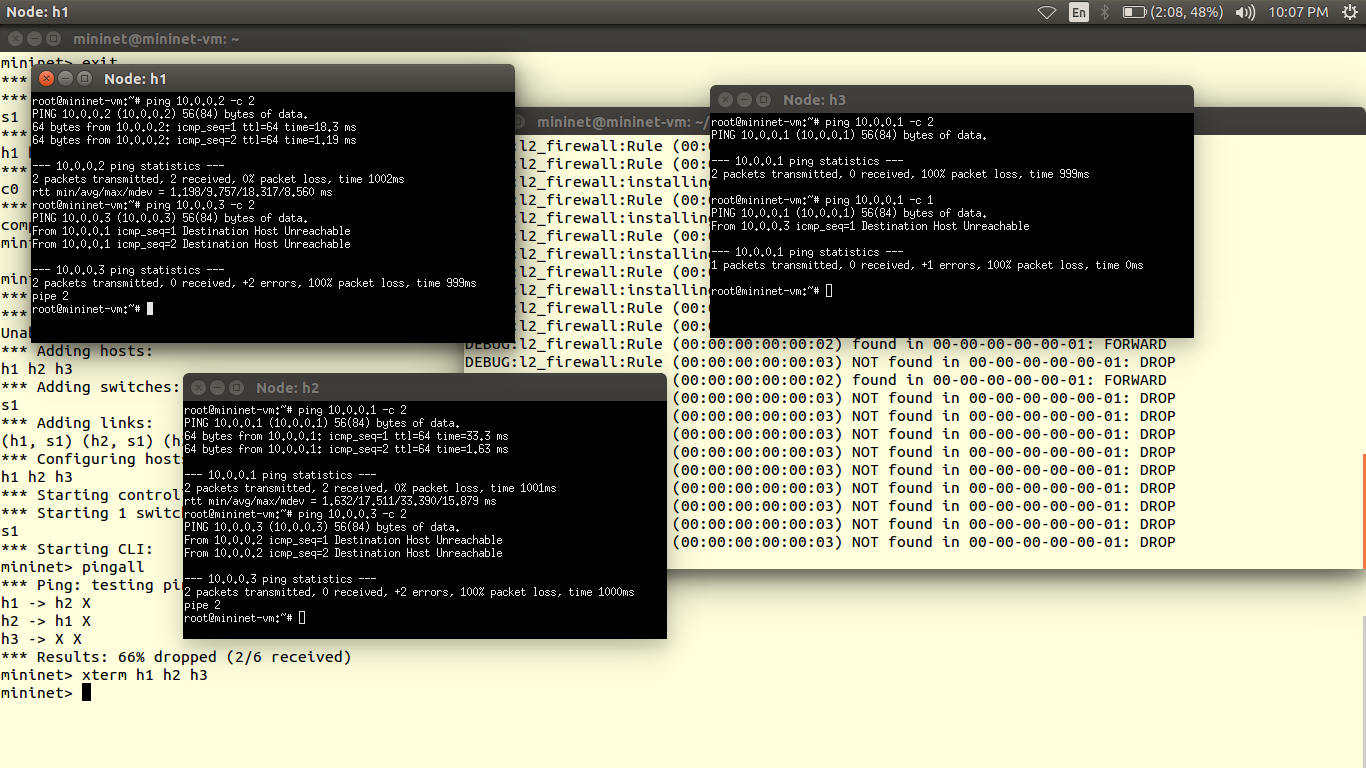
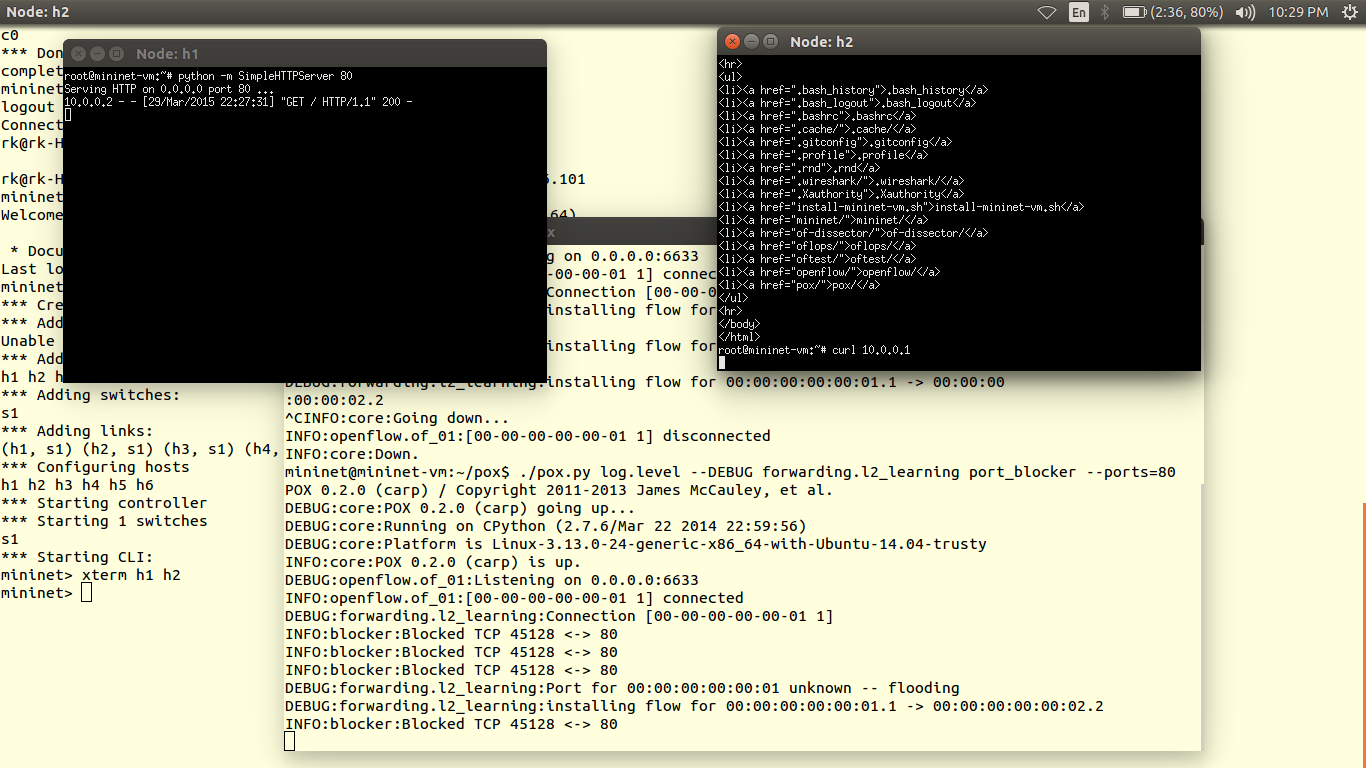
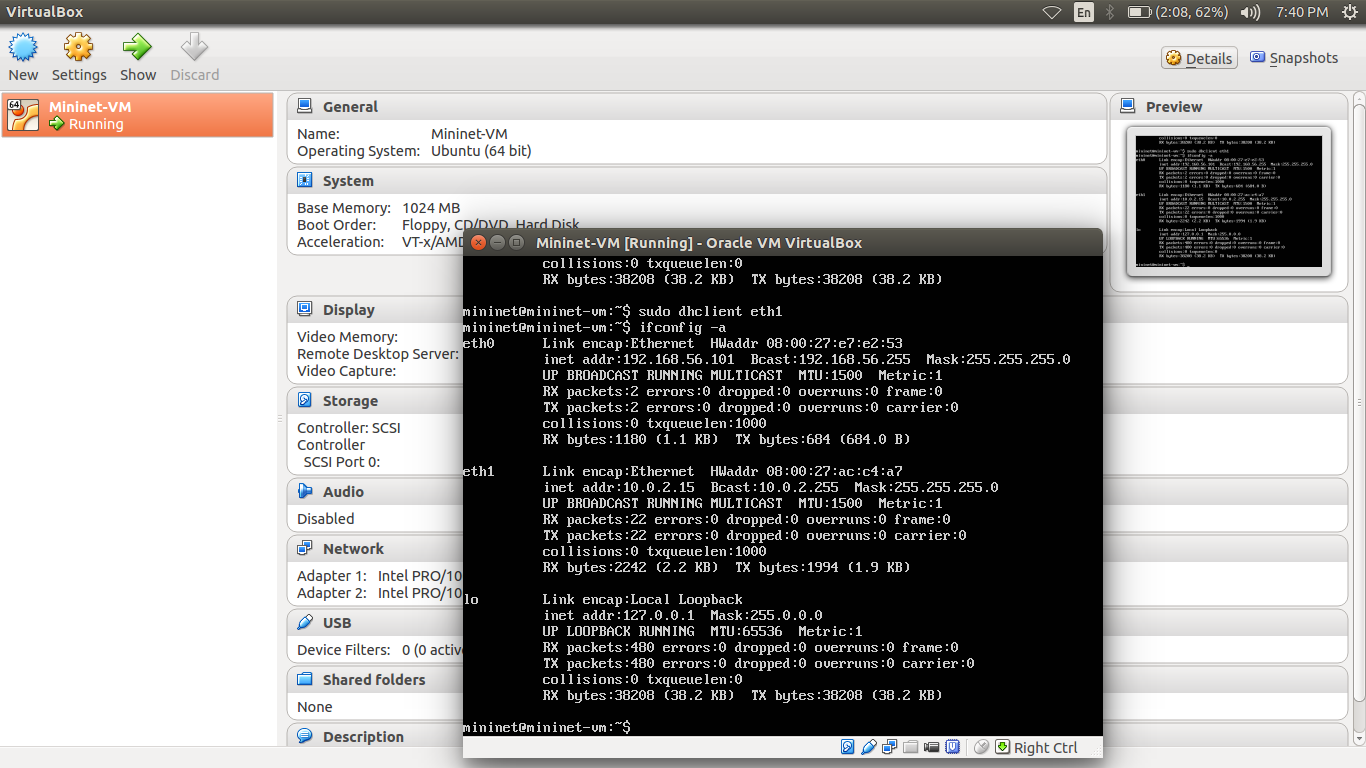
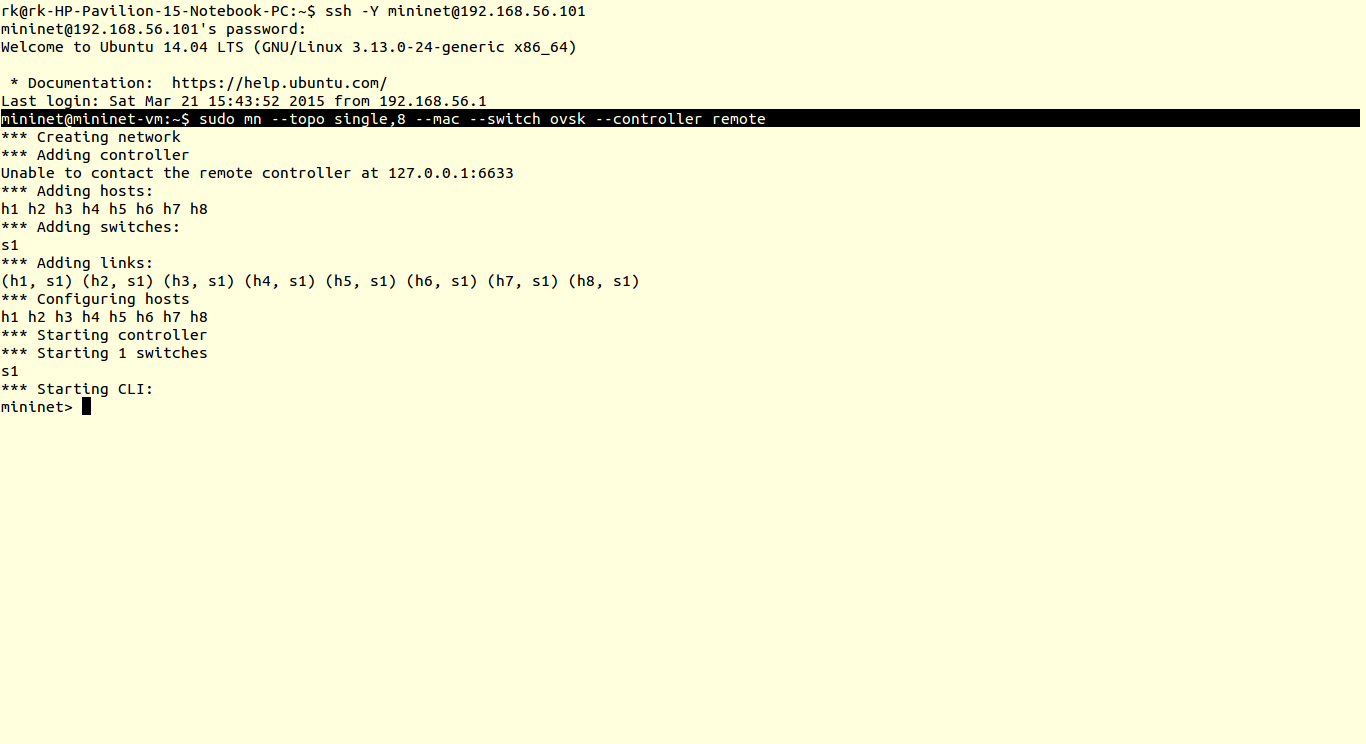
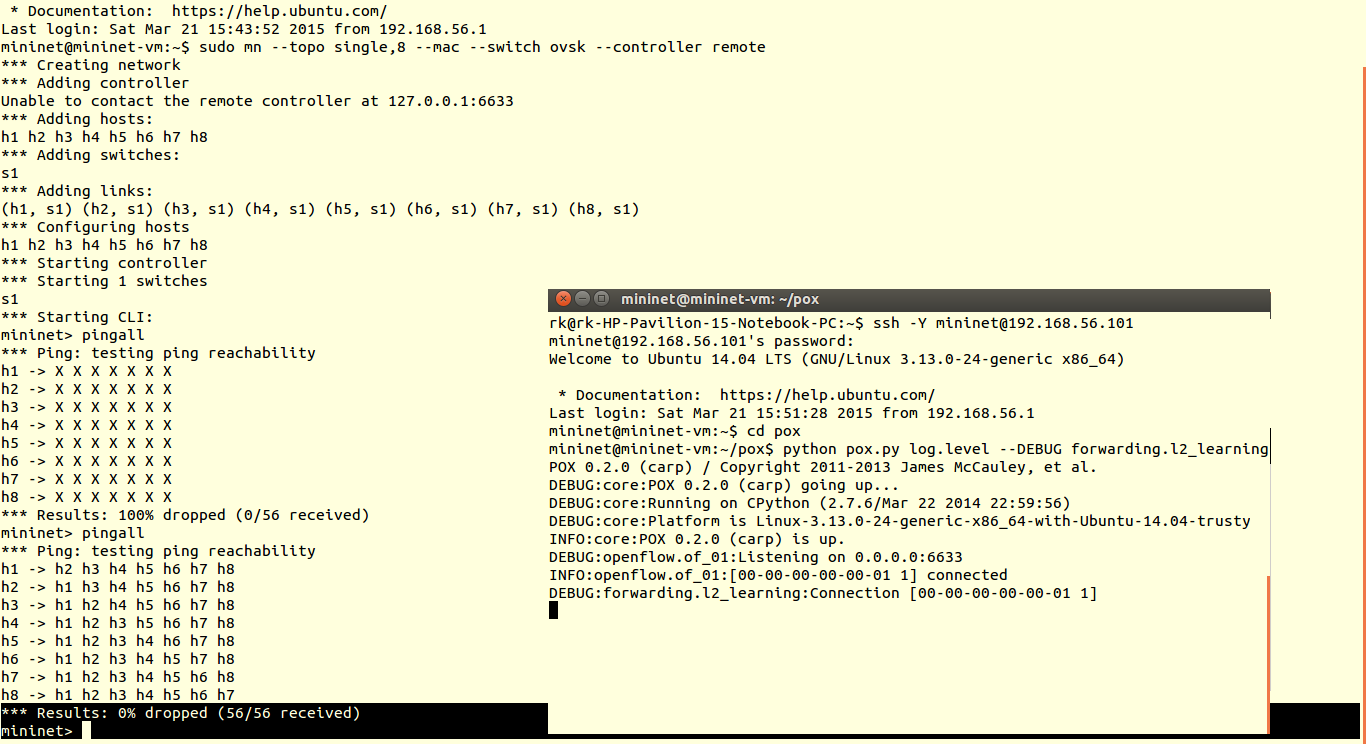
You can verify results using ping
This video tutorial will clear how to use VND.