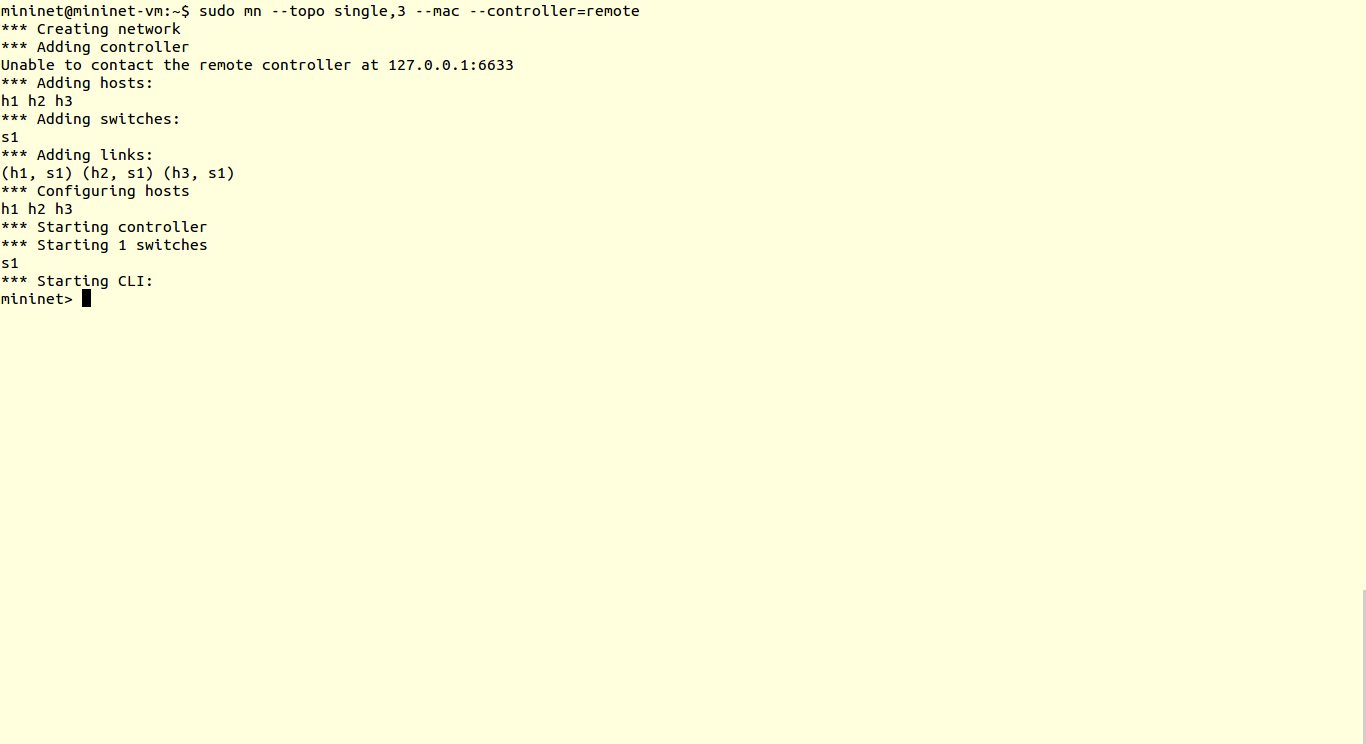
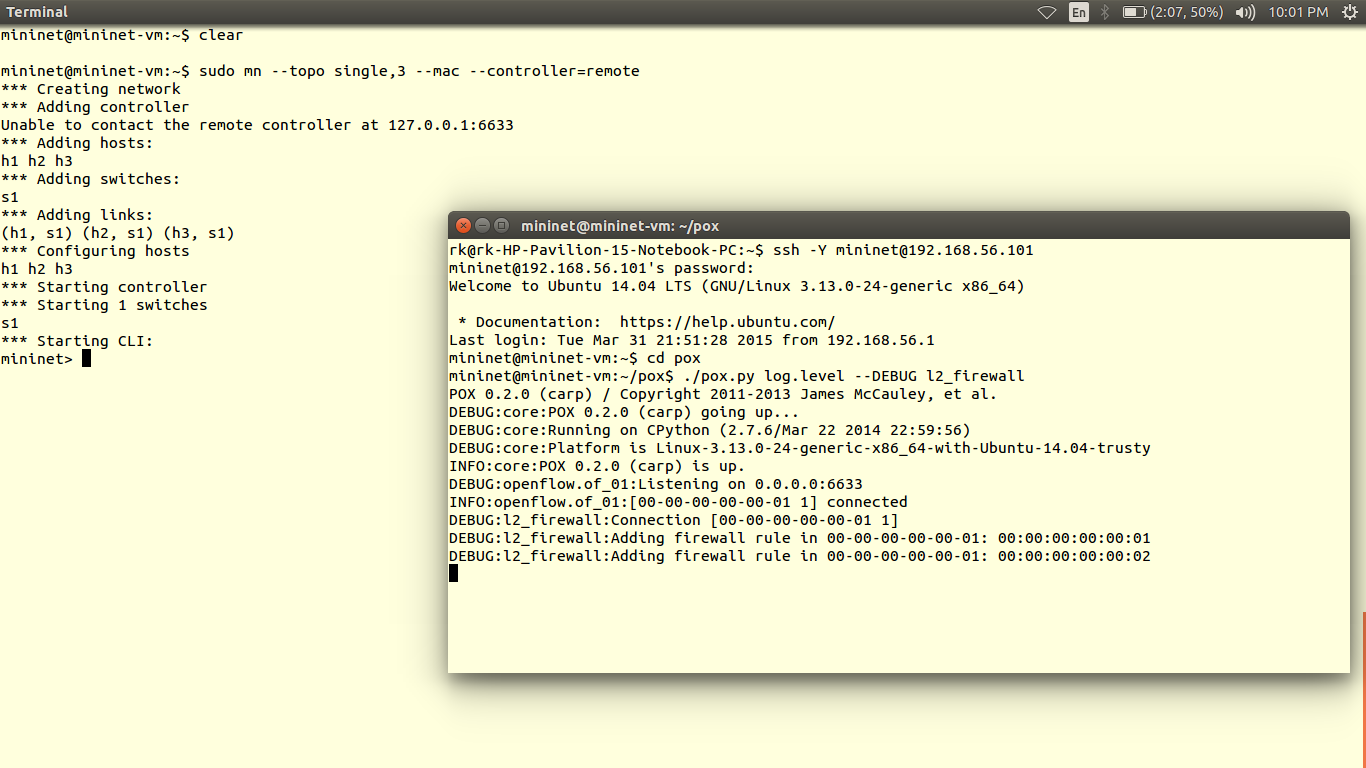
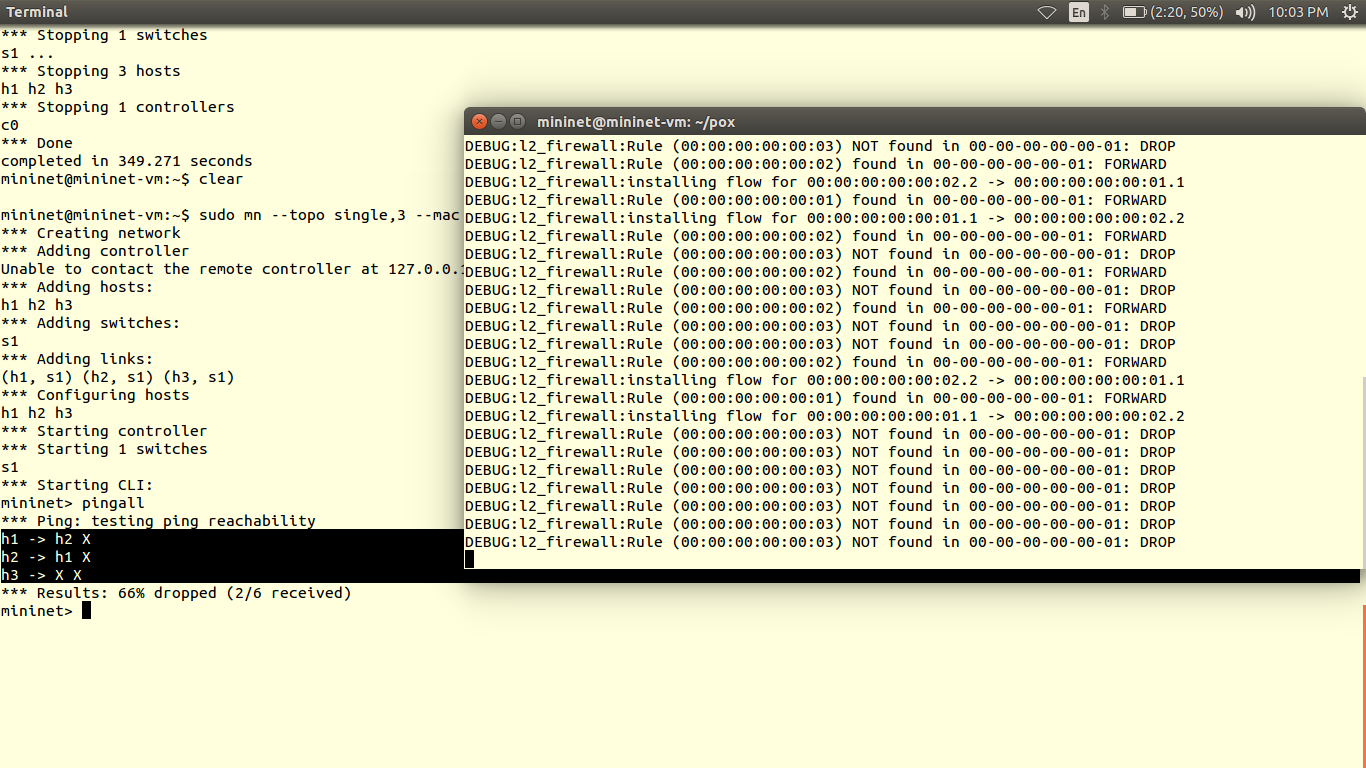
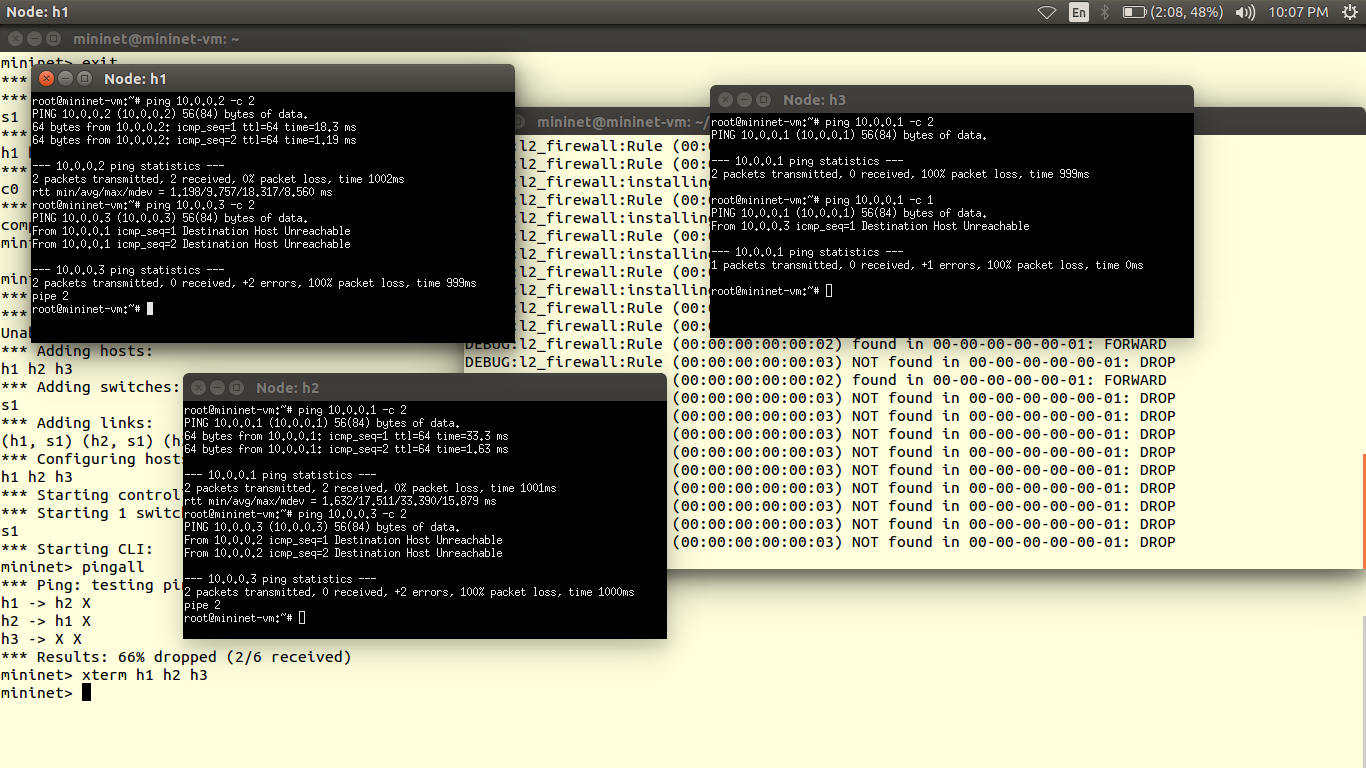
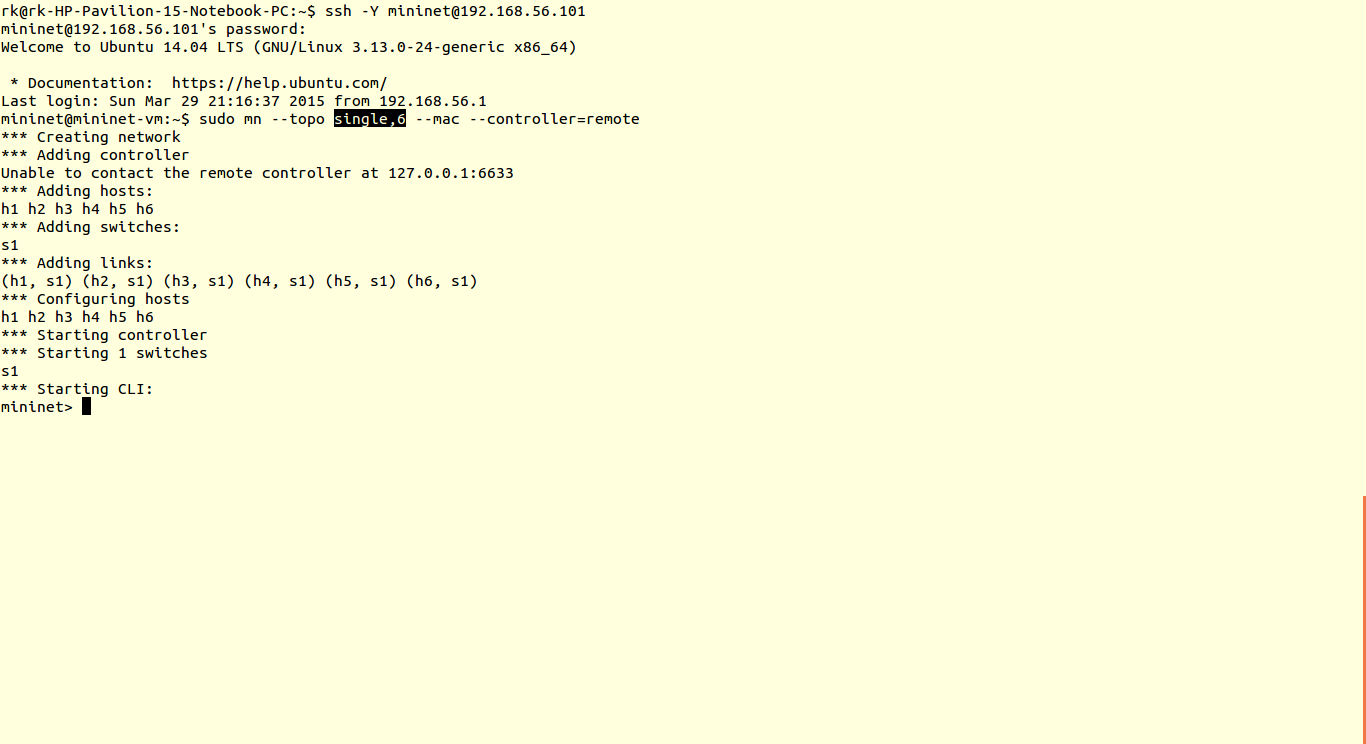
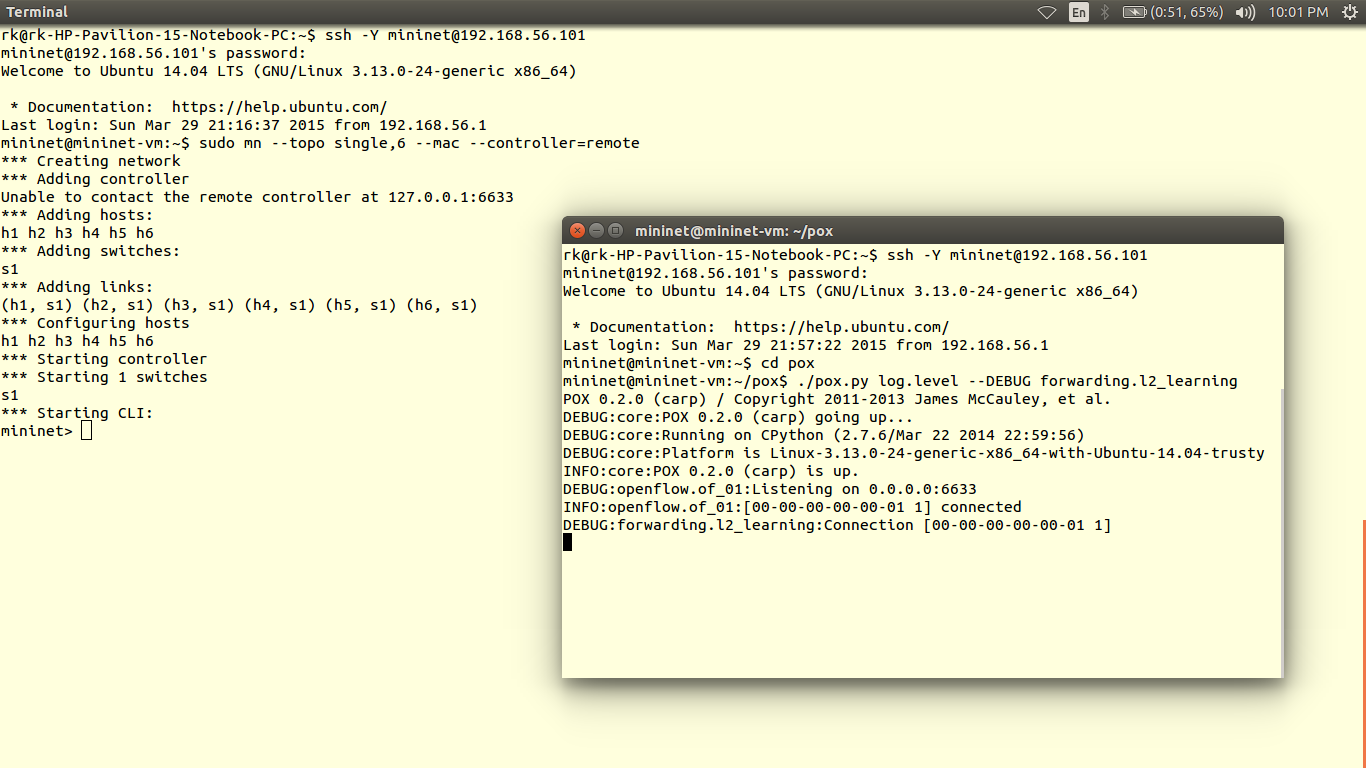
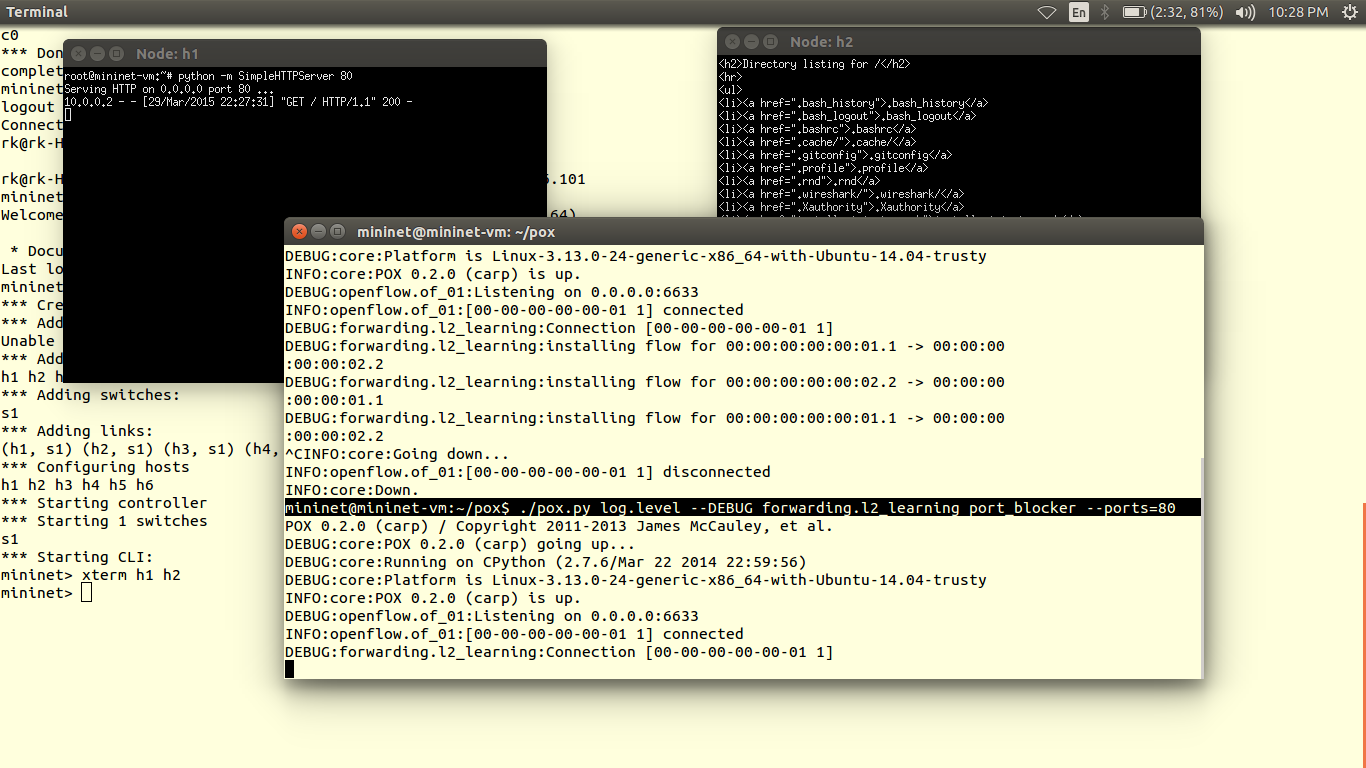
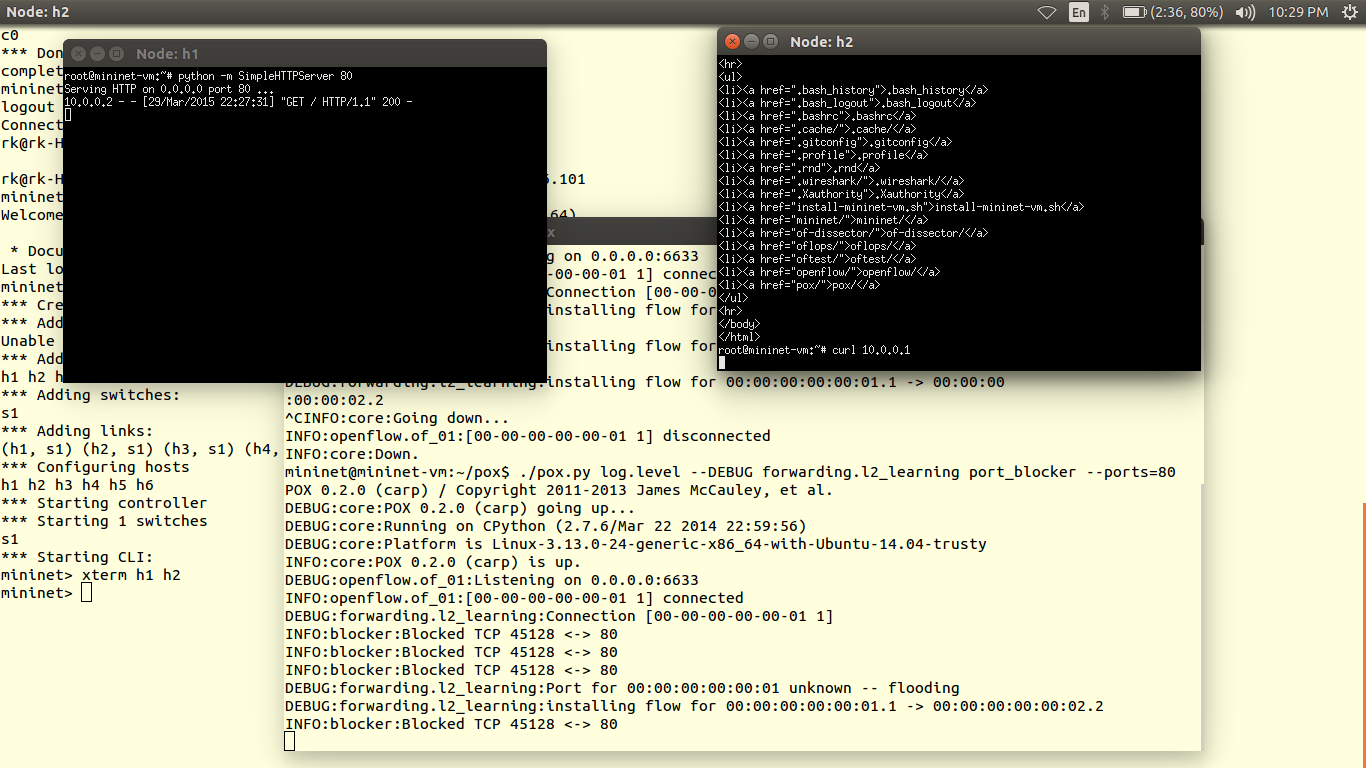
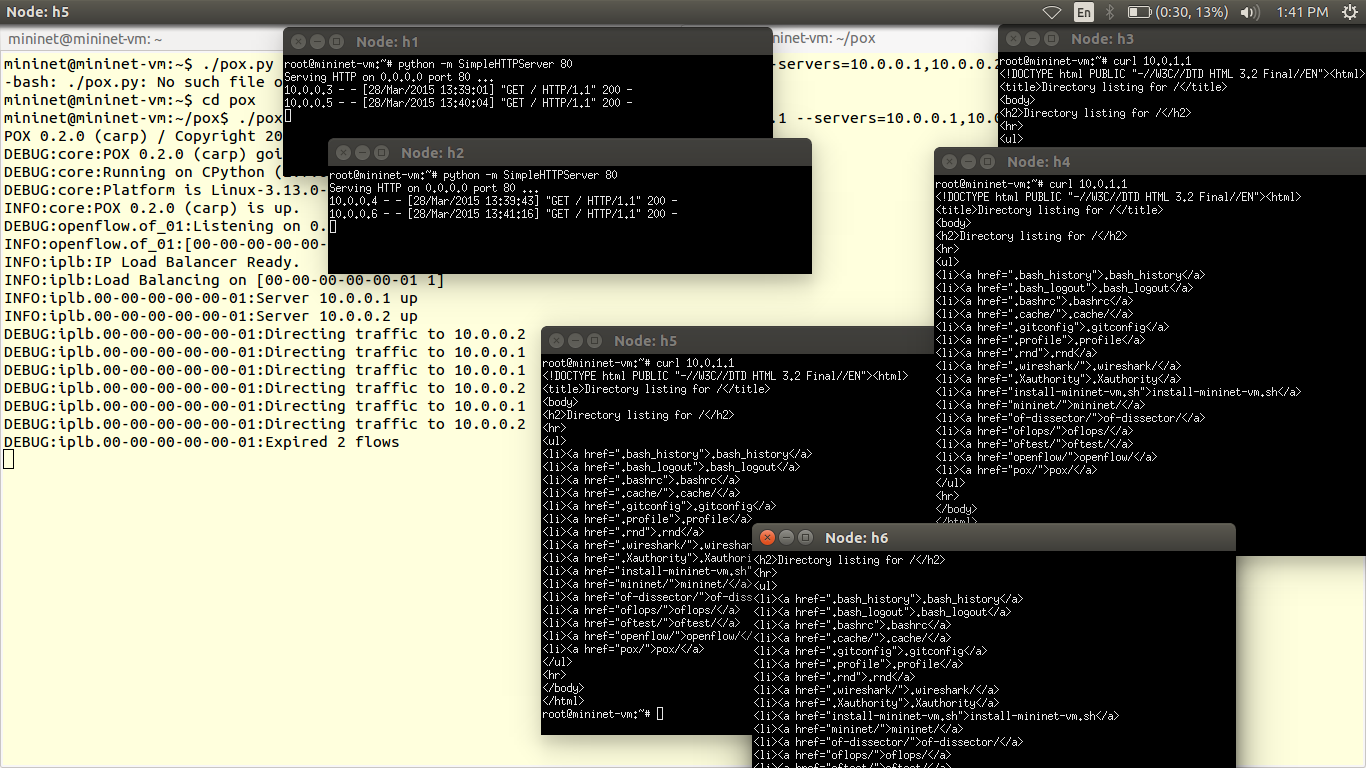
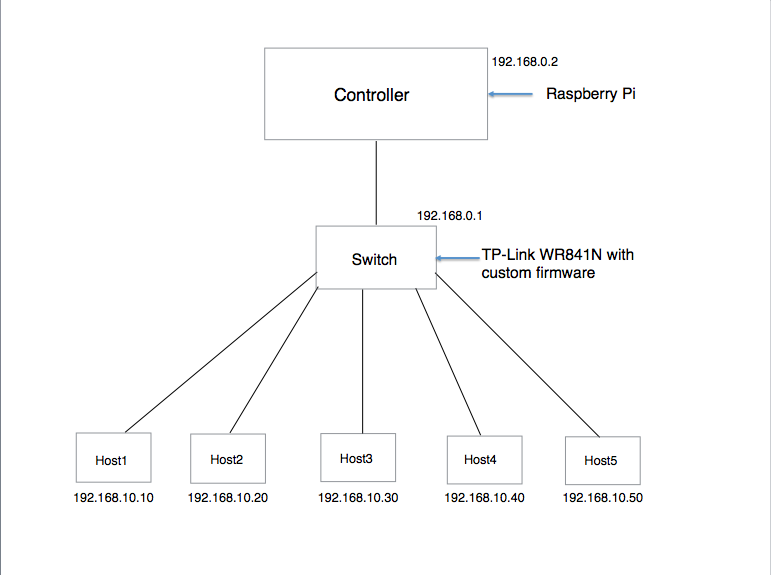
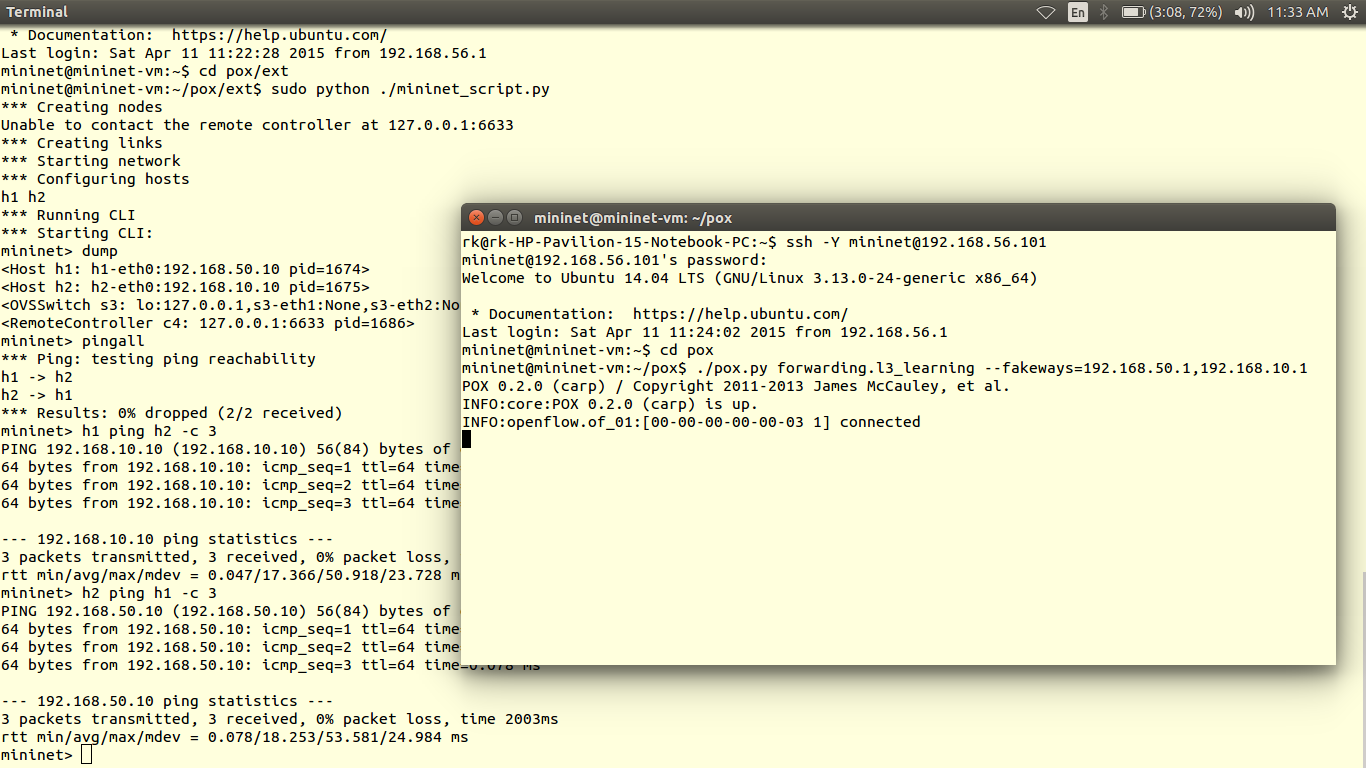
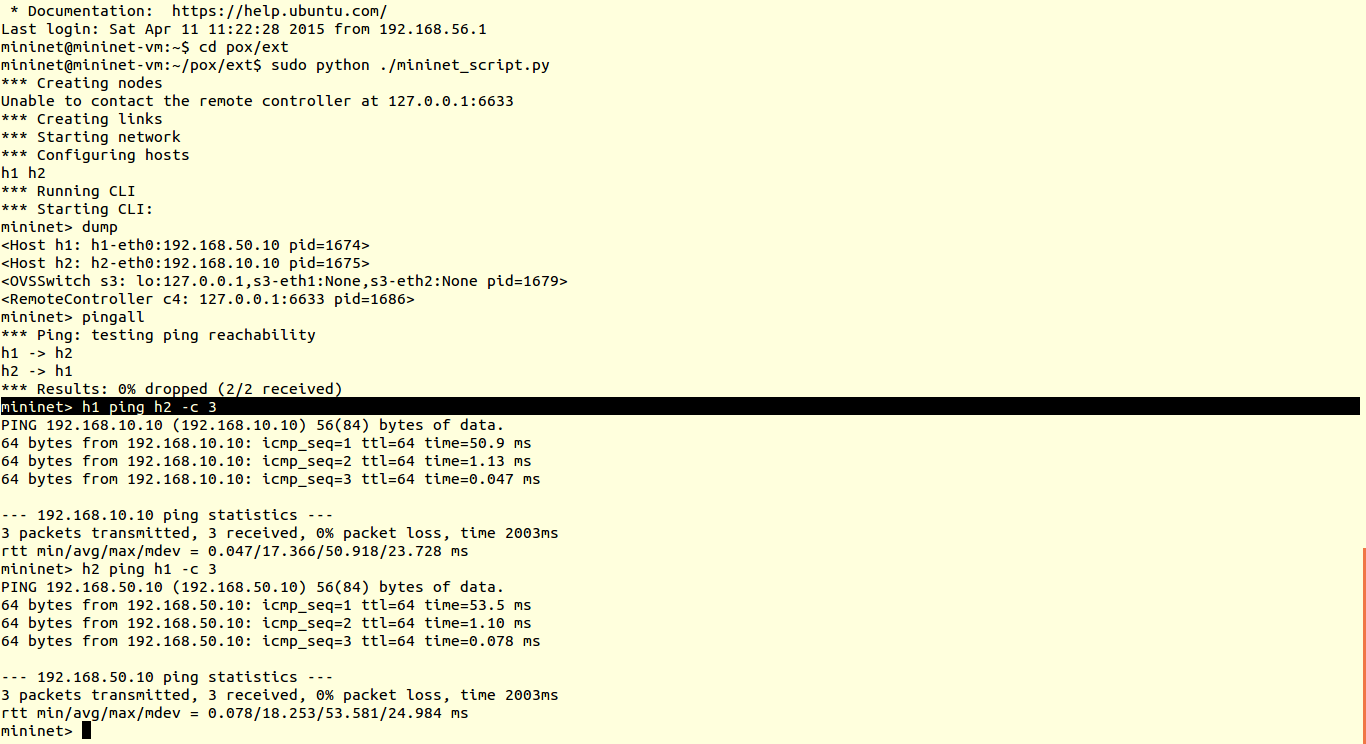
The data plane is represented by a router, as most of the routers are closed source we cannot use them out of the box. Hence we use OpenWRT which a open source linux based firmware for unmanageable routers. Prebuilt images of openwrt with openflow 1.0 for LinkSys WRT54GL,TP-LINK TL- WR1043ND (v1.7),TP-LINK TL- WR1043ND (v1.8) are available here. For TP-link TL-WR841N, pre built images with OpenFlow 1.0 are V9, V10, V11. Otherwise you can flash stock Chaos Calmer 15.05 image and then install OpenFlow 1.0 or OpenFlow1.3 by simple command
opkg install <package name>
If your router is not listed you’ll have to build image from source as per instructions here
Its highly recommend to use TP-link TL-WR841N v9, instructions given in this article are intended for WR841 v9 specifically.
WARNING: Flashing an unofficial firmware voids your warranty,and could turn your router into useless ‘brick’. Perform the operation at your own risk.
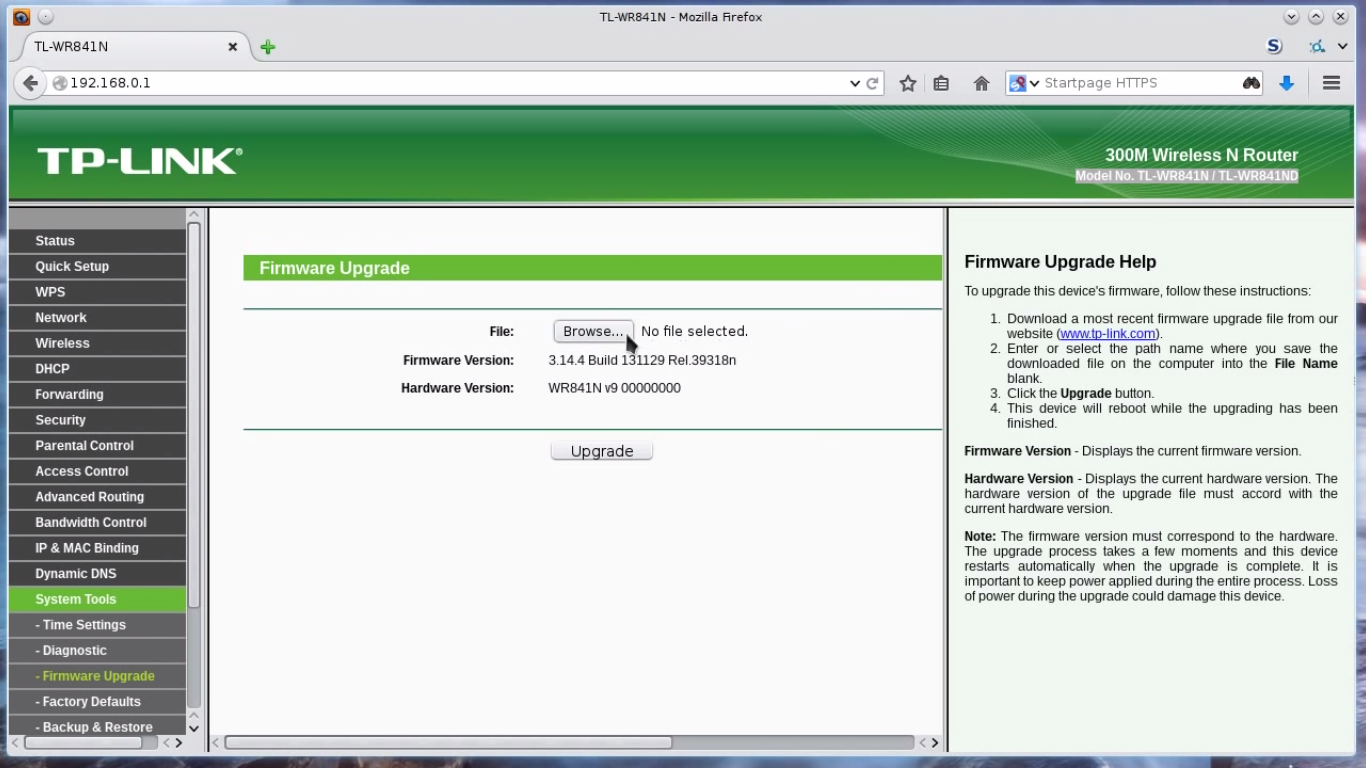
1.Connect your router to computer & point your browser to 192.168.0.1 ; login with credentials (Username:admin,Password:admin)
2.In left pane navigate to system tools –> Firmware upgrade, Check if the Hardware version is correct. Browse to the downloaded image final_image.bin & upgrade.
3.Refresh the page after process is completed,the tplink interface will vanish. Reboot router.
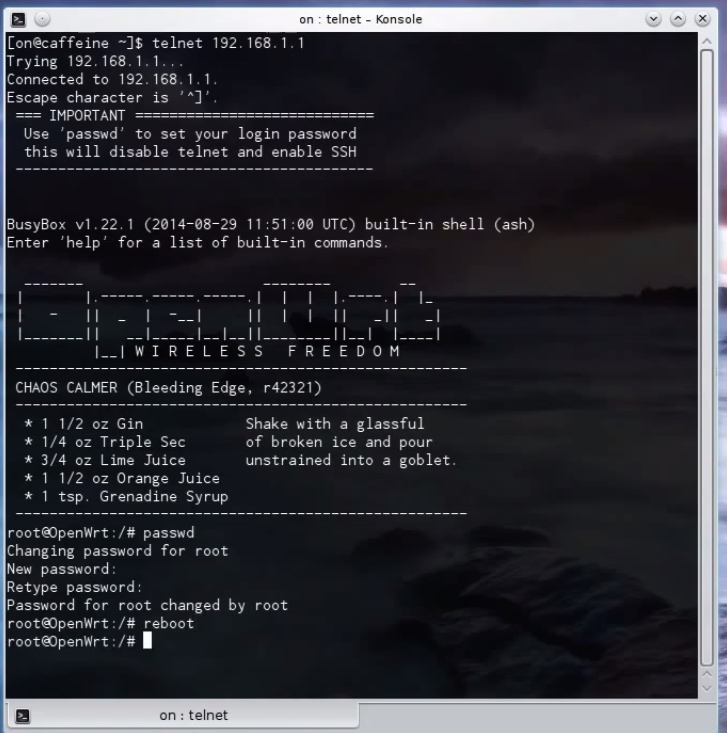
4. Through commnandline/terminal run
telnet 192.168.1.1
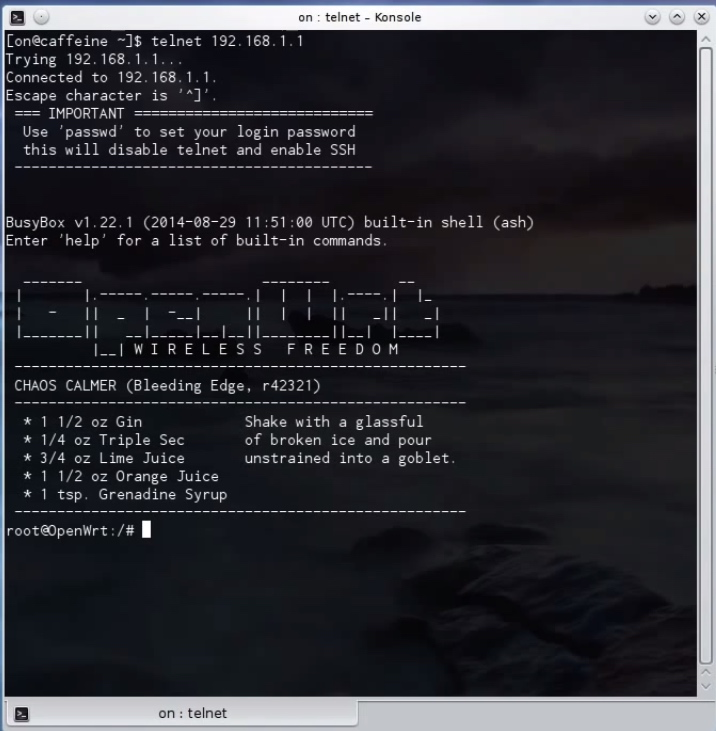
then set password for router access using
passwd
then exit the router using command ‘exit’. To get access of router after this you’ll have to use
ssh root@192.168.1.1
Now following two steps are specific to OpenFlow 1.0 to avoid slicing error. 1) Copy functions.sh from lib to etc [25].
# cp /lib/functions.sh /etc
2) Add –no-slicing parameter to /lib/openflow/ofswitch.sh [26]. After the addition of this parameter, the modified lines should look as follows.
if [[ "$mode" == "inband" ]]
then
echo "Configuring OpenFlow switch for inband control"
[ -n "$dpid" ] && {
ofdatapath punix:/var/run/dp0.sock -i "$dpports" --no-slicing
--local-port=tap:tap0 "--pidfile=$pidfile" -d "$dpid" &
}||{
ofdatapath punix:/var/run/dp0.sock -i "$dpports" --no-slicing
--local-port=tap:tap0 "--pidfile=$pidfile" &
}
else
echo "Configuring OpenFlow switch for out-of-band control"
[ -n "$dpid" ] && {
ofdatapath punix:/var/run/dp0.sock -i "$dpports" --no-slicing
--no-local-port "--pidfile=$pidfile" -d "$dpid" &
}||{
ofdatapath punix:/var/run/dp0.sock -i "$dpports" --no-slicing
--no-local-port "--pidfile=$pidfile" &
}
To set configuration of router
1.Edit the openflow file
vi /etc/config/openflow
enter ip address of raspberry pi instead of 192.168.0.2
config 'ofswitch'
option 'dp' 'dp0'
option 'dpid' '000000000009'
option 'ofports' 'eth1 wlan0 wlan0-1 wlan0-2'
option 'ofctl' 'tcp:192.168.0.2:6633'
option 'mode' 'outofband'2. Edit the network configuration file
vi /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config interface 'lan'
option ifname 'eth0.1'
option proto 'static'
option type 'bridge'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
config interface 'wifi'
option proto 'static'
config interface 'lan2'
option ifname 'eth0.2'
option proto 'static'
config interface 'lan3'
option ifname 'eth0.3'
option proto 'static'
config interface 'lan4'
option ifname 'eth0.4'
option proto 'static'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config switch
option name 'eth0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'eth0'
option vlan '1'
option ports '1 0t'
config switch_vlan
option device 'eth0'
option vlan '2'
option ports '2 0t'
config switch_vlan
option device 'eth0'
option vlan '3'
option ports '3 0t'
config switch_vlan
option device 'eth0'
option vlan '4'
option ports '4 0t'
3.Edit the wireless configuration
vi /etc/config/wireless
config wifi-device radio0
option type mac80211
option channel 11
option hwmode 11g
option path 'platform/qca953x_wmac'
option htmode HT20
option disabled 0
config wifi-iface wlan0
option device radio0
option network wifi
option mode ap
option ssid OpenWrtOne
option encryption none
config wifi-iface wlan2
option device radio0
option network wifi
option mode ap
option ssid OpenWrtTwo
option encryption none
config wifi-iface wlan3
option device radio0
option network wifi
option mode ap
option ssid OpenWrtThree
option encryption none
config wifi-iface wlan5
option device radio0
option network lan
option mode ap
option ssid OpenWrtXS
option encryption psk2
option key openwrtxs